Author: Cybernoz
AI code assistants integrated into IDEs, like GitHub Copilot, offer powerful chat, auto-completion, and test-generation features. However, threat actors and…
Source code is a critical asset for every company, and platforms like GitHub and Atlassian serve as secure vaults for it. Organizations…
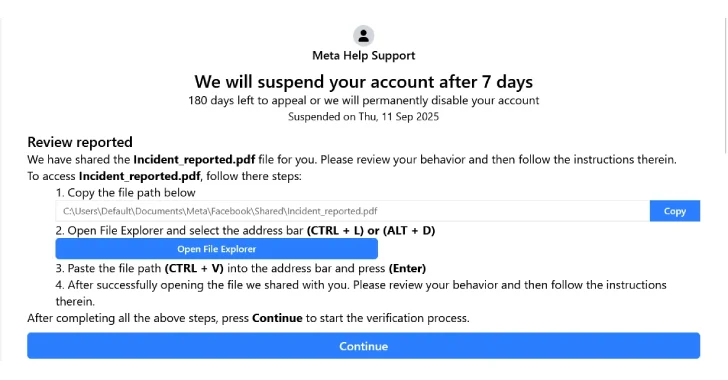
Sep 16, 2025Ravie LakshmananMalware / Social Engineering Cybersecurity researchers have warned of a new campaign that’s leveraging a variant of…
Turkey has tightened government control over telecommunications in recent weeks, preceding its moves with official statistics that seemed to vindicate…
The notorious cybercrime groups Scattered Spider and ShinyHunters claim they are retiring, but the cybersecurity industry is skeptical and believes…
Apple has released security updates to backport patches released last month to older iPhones and iPads, addressing a zero-day bug…
A critical vulnerability has been discovered in LG’s WebOS for smart TVs, allowing an attacker on the same local network…
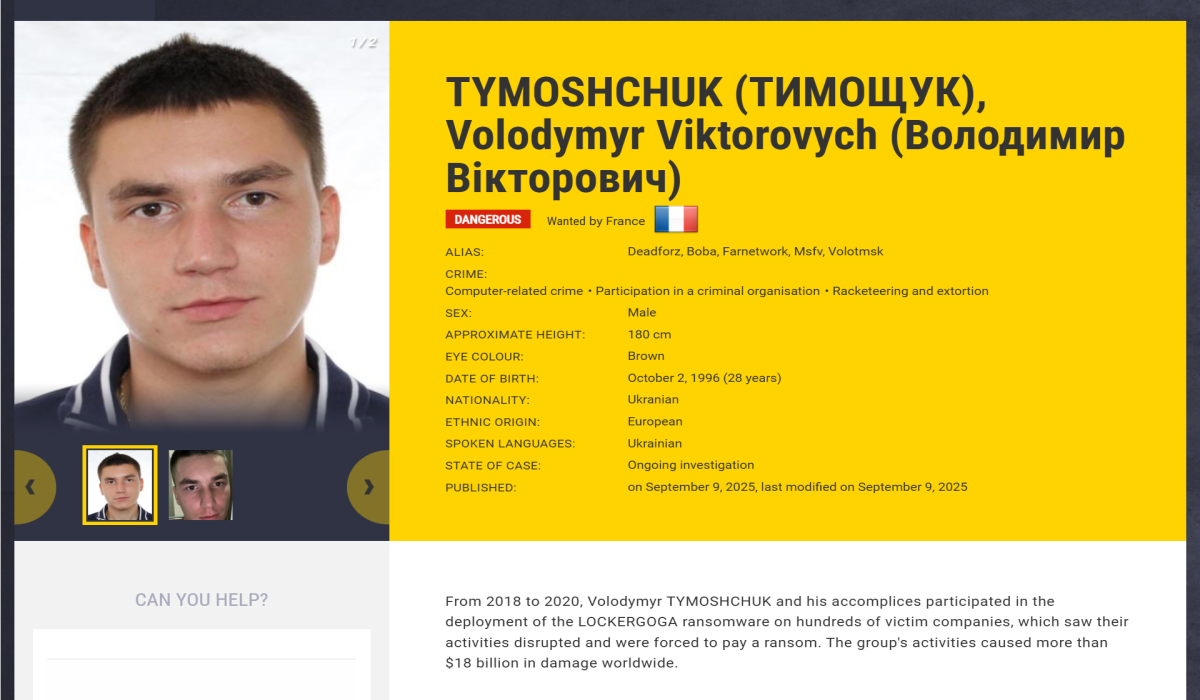
A Ukrainian man linked to one of the most destructive ransomware campaigns in recent years has now been singled out…
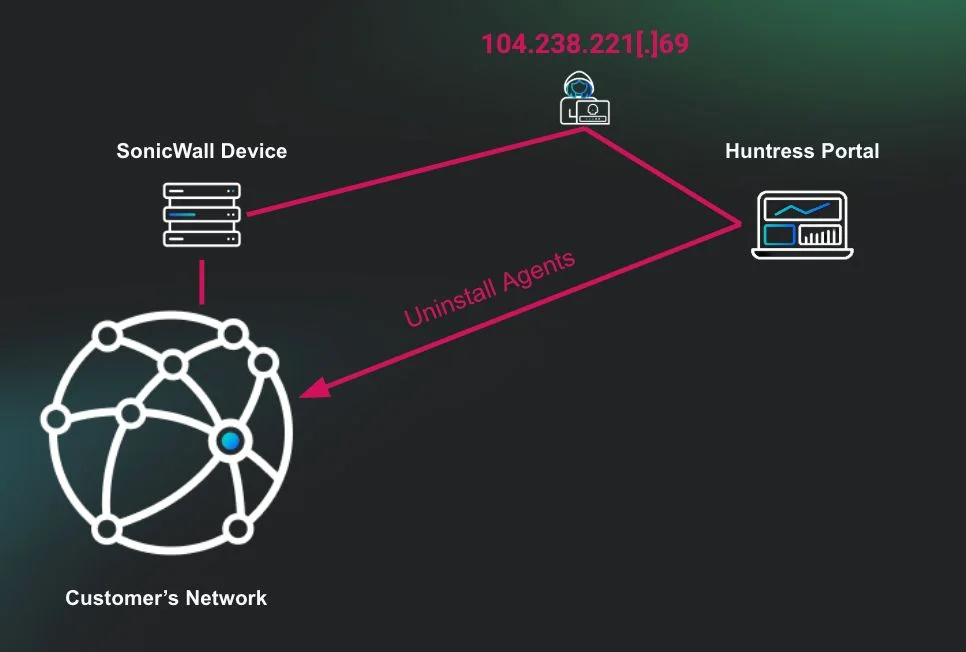
All target organizations are different, but ransomware attackers are highly adaptive and appreciate – and will exploit – any mistake…
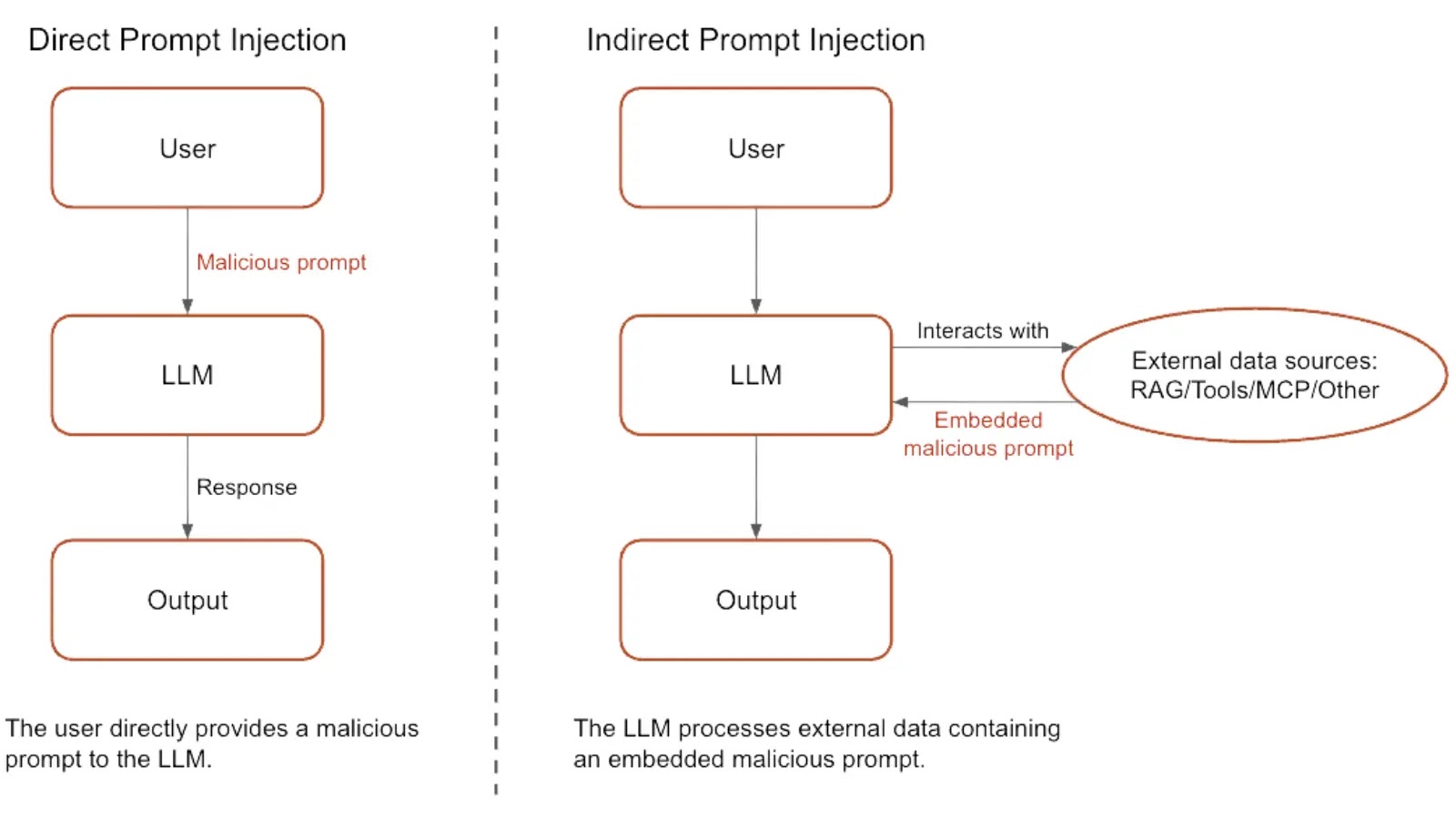
Sep 16, 2025The Hacker NewsAI Security / Enterprise Security AI agents are rapidly becoming a core part of the enterprise,…
A group of security researchers from the ETH Zurich university and Google have demonstrated a practical Rowhammer attack against DDR5….
A critical authentication bypass vulnerability in the Case Theme User WordPress plugin has emerged as a significant security threat, allowing…