Author: Cybernoz
A massive cyber fraud operation targeting Indians in Cambodia has emerged, with an estimated Rs 500 crore stolen in six…
Clearpool, a leading on-chain credit marketplace, is thrilled to announce its expansion to Avalanche with an exclusive launch of its…
02 Apr Story Of The First RSA Conference Told By Jim Bidzos This week in cybersecurity from the editors at…
The UK and US governments have agreed to collaborate on artificial intelligence (AI) safety. A memorandum of understanding, signed on…
Women represent only 30% of the global cybersecurity workforce, reflecting a slow growth rate and pervasive social inequalities. As we…
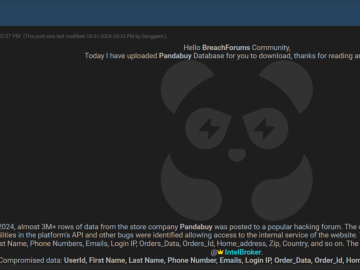
PandaBuy, a popular online shopping platform, has been the victim of a significant data breach. This breach has resulted in…
Image credit: Hackread.com Indian authorities rescue hundreds trafficked for cybercrime in Cambodia. Victims lured by false jobs, forced to work…
Apr 02, 2024NewsroomCyber Espionage / Threat Intelligence A threat activity cluster tracked as Earth Freybug has been observed using a…
Multinational Finnish industrial groups Outokumpu, Metsä and HKScan, are scaling-up deployment of artificial intelligence (AI) to drive international growth and…
The popular online shopping platform PandaBuy allegedly fell victim to a massive data breach, leaving over 1.3 million users affected….
Google agreed to erase billions of browser records to settle a class action lawsuit Pierluigi Paganini April 02, 2024 Google…
Microsoft has unveiled a suite of new tools within its Azure AI Studio. These innovations are designed to address the…