Author: Cybernoz
Hackers have been found leveraging Microsoft OneNote files as a vector to compromise systems across various industries. The campaign, under…
March 29, 2024 – Cybercriminals have taken MFA bombing to the next level by calling victims of an attack from…
A new keylogging server and client tool have been released on GitHub for pentesters. The tool utilizes DNS tunneling to…
Here’s a look at the most interesting products from the past month, featuring releases from: Appdome, AuditBoard, Bedrock Security, Cado…
The Android banking trojan known as Vultur has resurfaced with a suite of new features and improved anti-analysis and detection…
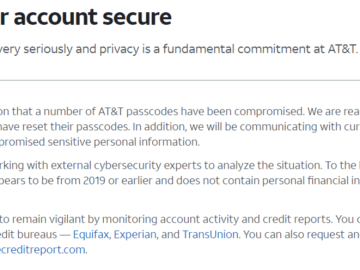
Telecommunications giant AT&T has confirmed a data breach affecting 73 million accounts. The company’s official press release confirms the AT&T…
AT&T has confirmed that personal data from approximately 73 million current and former customers has been leaked on the dark…
The ballistic missile hit the Rubymar on the evening of February 18. For months, the cargo ship had been shuttling…
Evasive, basic, and encrypted malware all increased in Q4 2023, fueling a rise in total malware, according to WatchGuard. Threat…
By Mr. Zakir Hussain, CEO – BD Software Distribution As digital landscapes morph and expand, cybersecurity challenges intensify. The fusion…
Over the past year, macOS users, particularly those in the cryptocurrency sector, have been increasingly targeted by infostealers. These malicious…
DinodasRAT, also known as XDealer, is a sophisticated C++ backdoor targeting multiple operating systems. It is designed to enable attackers…