Author: Cybernoz
Armed forces have always utilized war-gaming exercises for battlefield training to prepare for times of conflict. With today’s digital transformation,…
An automated risk detection system identified a typosquatting campaign targeting popular Python libraries on PyPI. In two waves with a…
Microsoft and OpenAI are working on plans for a data centre project that could cost as much as US$100 billion…
US telco AT&T is investigating a dataset released on the dark web about two weeks ago, saying a preliminary analysis…
The Indian government said it was rescuing its citizens who were lured into employment in Cambodia and were being forced…
The news that XZ Utils, a compression utility present in most Linux distributions, has been backdoored by a supposedly trusted…
The convenience and benefit of doing so much online these days, unfortunately, come with some risks. The crime of stealing…
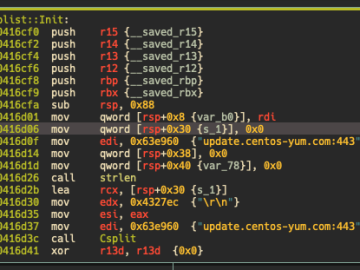
DinodasRAT Linux variant targets users worldwide Pierluigi Paganini March 31, 2024 A Linux variant of the DinodasRAT backdoor used in attacks against…
Security researchers have observed Red Hat and Ubuntu systems being attacked by a Linux version of the DinodasRAT (also known…
Building a Secure Last Mile for Global Commerce By Dan O’Toole, Chairman & CEO, Arrive Navigating the Last Mile: Securing…
By Gautam Hazari, Chief Technology Officer, Sekura.id Imagine, you are sitting in a café, sipping the skillfully crafted coffee by…
Image credit: Siyuan via Unsplash. Not AI. Generative AI services like Midjourney and OpenAI’s DALL-E can deliver the unimaginable when it comes to…