Author: Cybernoz
Organised by Eskenzi PR in media partnership with the IT Security Guru, the Most Inspiring Women in Cyber Awards aim to shed light…
GlorySprout stealer, advertised on the XSS forum in early March 2024, is a C++ stealer sold for $300 with lifetime…
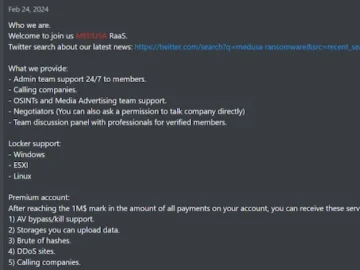
Smaller RaaS groups are trying to recruit new and “displaced” LockBit and Alphv/BlackCat affiliates by foregoing deposits and paid subscriptions,…
Mar 20, 2024NewsroomCybercrime / Financial Security Cybersecurity researchers have discovered an updated variant of a stealer and malware loader called…
Greggs bakery chain has had to close some outlets and go cash-only after an IT problem meant it could not…
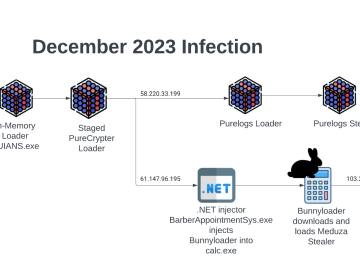
BunnyLoader 3.0 surfaces in the threat landscape Pierluigi Paganini March 20, 2024 Researchers found a new variant of the BunnyLoader malware with…
The makers of Flipper Zero have responded to the Canadian government’s plan to ban the device in the country, arguing…
The Chrome team has proudly announced that Chrome 123 has been promoted to the stable channel for users on Windows,…
Synopsys has unveiled Synopsys fAST Dynamic, a fresh addition to its dynamic application security testing (DAST) solutions within the Synopsys…
Operational Technology (OT) is a technology that interfaces with the physical world and includes Industrial Control Systems (ICS), Supervisory Control…
Ukrainian police seized a massive trove of 100 million stolen email and Instagram accounts – Three individuals were arrested for…
20 Mar Cybersecurity: An AI Stock To Buy And Hold Long Term This week in cybersecurity from the editors at…