Author: Cybernoz
While most tax payers don’t particularly look forward to tax season, for some scammers it’s like the opening of their…
Multiple threat actors are exploiting the recently disclosed security flaws in JetBrains TeamCity software to deploy ransomware, cryptocurrency miners, Cobalt…
A hospice in South Devon is working with Amazon Web Services (AWS) to create an artificial intelligence-enabled (AI) residential care…
CISA, alongside key partners such as the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), and various U.S….
Researchers investigated potential malicious uses of AI by threat actors and experimented with various AI models, including large language models,…
In April 2023, Microsoft announced that it would be undertaking a multi-year effort to reduce domain fragmentation among authenticated, user-facing Microsoft 365…
Mintlify data breach exposes GitHub tokens of 91 customers. The software documentation platform experienced a security vulnerability that compromised private…
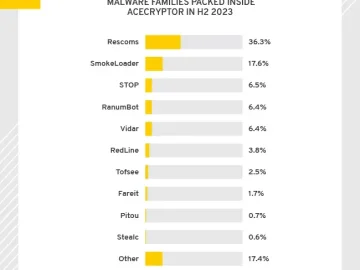
ESET Research has recorded a considerable increase in AceCryptor attacks, with detections tripling between the first and second halves of…
Earlier this week, the data of over 70 million people was posted for sale on an online cybercrime forum. The…
Mar 20, 2024The Hacker NewsArtificial intelligence / Webinar Did you know that 79% of organizations are already leveraging Generative AI…
Nations Direct Mortgage, LLC, found itself in the midst of a cybersecurity crisis in December 2023, as it grappled with…
**Disclaimer: The content of this blog post is for general information purposes only and is not legal advice. We are…