Author: Cybernoz
In February of this year, the Cybersecurity and Infrastructure Security Agency (CISA) revealed that its systems had been compromised by…
In the past few years, an increasing number of tech companies, organizations, and even governments have been working on one…
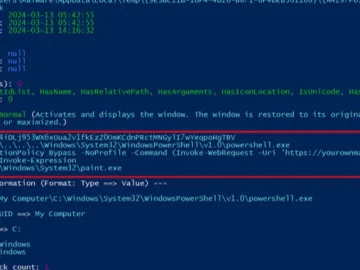
Mar 19, 2024NewsroomSocial Engineering / Email Security A new phishing campaign is targeting U.S. organizations with the intent to deploy…
Fujitsu, the renowned multinational technology giant, issued a statement on Friday confirming a cyberattack on its systems. The company’s officials…
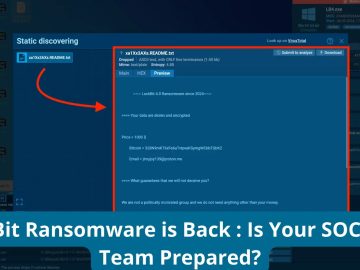
Law enforcement disrupted LockBit ransomware operations in February, seizing infrastructure and their website. Regretfully, the victory appears to have been…
In this Help Net Security interview, Pedro Cameirão, Head of Cyber Defense Center at Nokia, discusses emerging cybersecurity trends for…
Epic Games’ competition lawsuit against Apple and Google has finally opened in the Federal Court, with lawyers kicking off day…
The ongoing “free wedding invite” scam is one of several innovative campaigns aimed at the senior population. Through social media…
The Australian Signals Directorate has added Microsoft threat intelligence into its cyber threat intelligence sharing (CTIS) platform. The directorate said…
Extreme weather events and warnings from experts that keeping temperature rises below the 1.5°C limit is becoming increasingly difficult have…
A former IT support contractor to the Australian National Maritime Museum will spend at least 15 months behind bars over…
A sophisticated hacking campaign attributed to a Chinese Advanced Persistent Threat (APT) group known as ‘Earth Krahang’ has breached 70…