Author: Cybernoz
New high-performance malware “BunnyLoader 3.0” steals logins, crypto & lurks undetected. Palo Alto Unit 42 reveals its tricks to help…
For those prioritizing a secure browsing experience, here’s some promising news: Google has announced that Chrome users utilizing the safe…
Tools such as Open AI’s DALL.E 2, SORA and Chat GPT, Google’s Bard (now Gemini), and Microsoft’s Copilot, now make…
Moldovan national Sandu Boris Diaconu has been sentenced to 42 months in prison for operating E-Root, a major online marketplace…
HiddenLayer’s recent research has uncovered a series of concerning vulnerabilities within Google’s latest Large Language Models (LLMs) family, known as…
15 Mar When To Change Your Wi-Fi Password. Better Safe Than Sorry. This week in cybersecurity from the editors at…
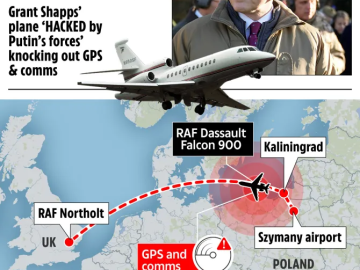
UK Defence Secretary jet hit by an electronic warfare attack in Poland Pierluigi Paganini March 15, 2024 Russian hackers have…
A new variant of StopCrypt ransomware (aka STOP) was spotted in the wild, employing a multi-stage execution process that involves…
AI tech fuels surge in financial fraud and cybercrime, warns INTERPOL. Sophisticated scams and human trafficking rings exploit cryptocurrency and…
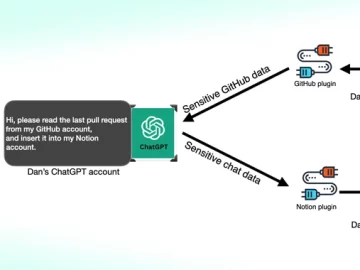
Mar 15, 2024NewsroomData Privacy / Artificial Intelligence Cybersecurity researchers have found that third-party plugins available for OpenAI ChatGPT could act…
A threat actor has surfaced on the dark web, announcing the creation of “Hell Paradise,” a covert online platform purportedly…
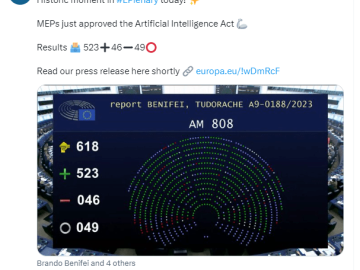
The European Parliament has approved the groundbreaking Artificial Intelligence (AI) Act, signaling a pivotal step towards regulating AI technologies while…