Author: Cybernoz
Carlsbad, California – Encina Wastewater Authority (EWA) found itself targeted by the notorious BlackByte ransomware group. The threat actor, known…
Cybersecurity experts have raised the alarm over a newly identified ransomware group, “Rabbit Hole,” which has been making headlines for…
In the ever-evolving landscape of cyber threats, organizations and governments worldwide are increasingly turning to collaborative efforts to combat the…
While the threat landscape continues to shift and evolve, attackers’ motivations do not, according to a Red Canary report. The…
Nissan Motor Corporation and Nissan Financial Services in Australia and New Zealand, collectively known as Nissan Oceania, have started reaching…
Here’s a look at the most interesting products from the past week, featuring releases from AuditBoard, Cynerio, DataDome, Regula, and…
Westpac has put its former Chatswood disaster recovery centre on the market. JLL Capital Markets is selling the facility at…
A new NBN price model approved late last year drove a mass behind-the-scenes shift in how TPG Telecom and Optus…
Cisco fixed high-severity elevation of privilege and DoS bugs Pierluigi Paganini March 14, 2024 Cisco this week addressed high-severity elevation…
Google enjoys a competitive edge in generative artificial intelligence due to its trove of data and AI-optimised chips, Microsoft has…
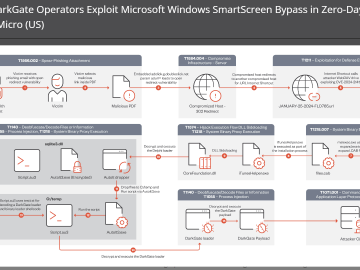
Recent DarkGate campaign exploited Microsoft Windows zero-day Pierluigi Paganini March 14, 2024 Researchers recently uncovered a DarkGate campaign in mid-January…
A new variant of StopCrypt ransomware (aka STOP) was spotted in the wild, employing a multi-stage execution process that involves…