Author: Cybernoz
Mar 14, 2024NewsroomRansomware / Cyber Crime A 34-year-old Russian-Canadian national has been sentenced to nearly four years in jail in…
NHS doctor Chris Day has won the right to challenge a tribunal decision which raises questions about information governance in…
Nissan Oceania is warning of a data breach impacting 100,000 people after suffering a cyberattack in December 2023 that was…
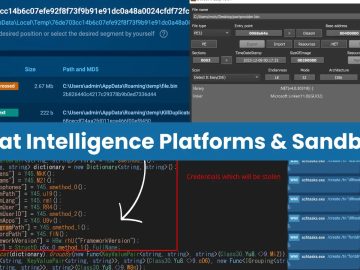
Organizations have many tools when investigating cyber threats, but two stand out: Threat Intelligence Platforms (TIPs) and sandboxes. Each solution…
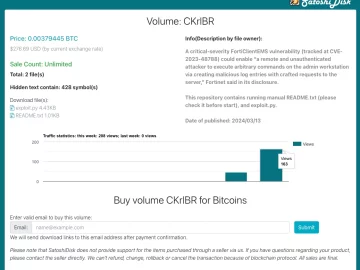
A recently fixed SQL injection vulnerability (CVE-2023-48788) in Fortinet’s FortiClient Endpoint Management Server (EMS) solution has apparently piqued the interest…
Mar 14, 2024NewsroomCyber Espionage / Malware The Russian-speaking cybercrime group called RedCurl is leveraging a legitimate Microsoft Windows component called…
France Travail, formerly known as Pôle Emploi, is warning that hackers breached its systems and may leak or exploit personal…
Threat actors have been observed hosting phishing documents on legitimate digital document publishing (DDP) sites as part of continuous session…
14 Mar 5 Of The Highest Paying Cybersecurity Jobs In 2024 This week in cybersecurity from the editors at Cybercrime…
Mar 14, 2024NewsroomContainer Security / Vulnerability Details have been made public about a now-patched high-severity flaw in Kubernetes that could…
Recognizing the vital role of Emergency Communications Centers (ECCs) in public safety, the Cybersecurity and Infrastructure Security Agency (CISA), in…
A dark web actor recently unveiled a trove of more than 15,500 debit and credit cards allegedly linked to Mexican…