Author: Cybernoz
Threat actors target Notepad++ as it is a widely used text editor among developers and users, offering a large potential…
The “State of the UAE—Cybersecurity Report 2024,” a collaborative effort by the UAE Cyber Security Council and CPX Holding, has…
Mar 14, 2024The Hacker NewsVulnerability / Network Security Fortinet has warned of a critical security flaw impacting its FortiClientEMS software…
The children of former subpostmasters whose lives were ruined by the Post Office Horizon scandal have come together to form…
Hamilton, which is recognized for its resilience, has shifted its focus from responding to a recent ransomware assault to recovery,…
Nissan Motor Corporation and its financial services in Australia and New Zealand, collectively known as Nissan Oceania, have been the…
Hackers target these platforms due to their hosting of valuable resources and data. For financial gain or some other bad…
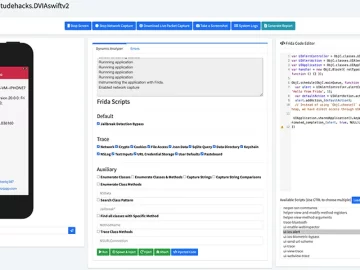
The Mobile Security Framework (MobSF) is an open-source research platform for mobile application security, encompassing Android, iOS, and Windows Mobile….
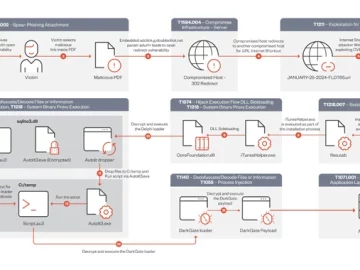
Mar 14, 2024NewsroomMalware / Cyber Attack A DarkGate malware campaign observed in mid-January 2024 leveraged a recently patched security flaw…
Streaming service giant Roku recently experienced a data breach affecting over 15,000 user accounts. Between December 28, 2023, and February…
Up to 100,000 Australian and New Zealand customers may have been affected by Nissan’s December cyber incident. The company first…
HackerOne Brand Ambassadors are leaders who have a passion to bring the community together in their local city or region….