Author: Cybernoz
Rust’s strong focus on memory safety, which prevents common vulnerabilities such as buffer overflows, makes it a choice for threat…
An infostealer disguised as the Adobe Reader installation has been observed. The file is disseminated in PDF format and prompts users…
The South Australian government has begun its long-awaited enterprise resource planning (ERP) replacement, with Oracle to provide the platform. In…
Microsoft’s patch cycle this month has a handful of notable vulnerabilities – apparently none of them zero-days – in a…
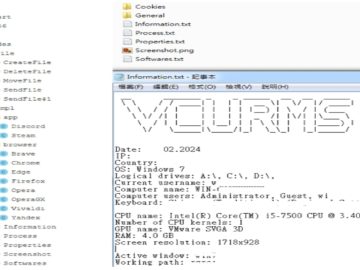
Cybersecurity researchers at Fortinet’s FortiGuard Labs have discovered a new threat called Vcurms malware targeting popular browsers and apps for…
Software developers who use Apple’s App Store will soon be able to distribute apps to EU users directly from their…
The KB5035849 cumulative update released during today’s Patch Tuesday fails to install on Windows 10 and Windows Server systems with…
February was a particularly busy month for search-based malvertising with the number of incidents we documented almost doubling. We saw…
China could use social media app TikTok to influence the 2024 US elections, US director of national intelligence Avril Haines…
Brave has seen a sharp increase in users installing its privacy-focused Brave Browser on iPhones after Apple introduced changes to…
Oracle soared more than 13 percent to reach a record high on signs the company was making progress in its…
Microsoft Patch Tuesday security updates for March 2024 fixed 59 flaws Pierluigi Paganini March 12, 2024 Microsoft Patch Tuesday security…