Author: Cybernoz
Ibis Budget guests were left vulnerable after a security flaw in self-check-in kiosks exposed room access codes. Learn how this…
Microsoft has confirmed that some Outlook.com users are experiencing issues with emails being blocked and marked as spam when trying…
Telecommunications giant AT&T has finally confirmed that 73 million current and former customers have been caught up in a massive…
HSBC Bank has been caught out by poor data quality, leading to fines for Consumer Data Right (CDR) breaches. The…
Governance, risk and compliance (GRC) cybersecurity professionals play a vital role in organizations, aligning IT goals with objectives as they…
Government ministers in migration and biosecurity are facing scrutiny over their ability to outsource some decisions, or aspects of decisions,…
US prosecutors were able to charge FTX founder Sam Bankman-Fried shortly after the cryptocurrency exchange’s collapse in part because they…
Omni Hotels & Resorts has been experiencing a chain-wide outage that brought down its IT systems on Friday, impacting reservation,…
Amazon Web Service (AWS) has expanded its free credits program for startups to cover the costs of using major AI…
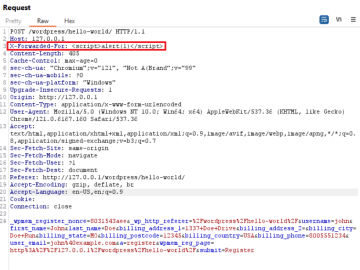
XSS flaw in WordPress WP-Members Plugin can lead to script injection Pierluigi Paganini April 02, 2024 A cross-site scripting vulnerability…
Powerloom, a leading composable data network that enables protocols to index and query blockchain data in a decentralized manner, today…
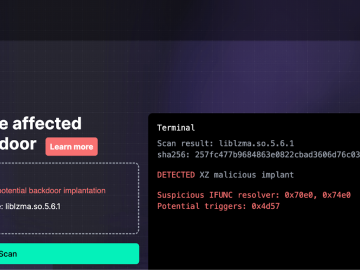
Binarly released the free online scanner to detect the CVE-2024-3094 Backdoor Pierluigi Paganini April 02, 2024 Researchers from the firmware…