Author: Cybernoz
By Kevin Beasley, CIO, VAI Increased competition and new regulatory requirements are increasing the tempo of digital transformation among mid-market…
Hackers exploit unpatched Ivanti vulnerabilities to deploy malware on Linux systems. Magnet Goblin targets businesses using outdated software. Patch immediately…
Attack Surface Management, Dark Web Monitoring, and Application Penetration Testing by Dr. Ilia Kolochenko, CEO and Chief Architect, ImmuniWeb ImmuniWeb…
But what, then, were those programs? Herein lies the most intriguing—and potentially ground-breaking—question that the Pentagon study leaves us wondering:…
Named Microsoft’s Security Impact Partner of the Year in 2023 for delivering excellence and innovative end-to-end security, Difenda is proud…
Roku has disclosed a data breach impacting over 15,000 customers after hacked accounts were used to make fraudulent purchases of…
As of 2024, Birmingham City Council is one of a number of local authorities facing a financial crisis. Local services…
Organised by Eskenzi PR in media partnership with the IT Security Guru, the Most Inspiring Women in Cyber Awards aim…
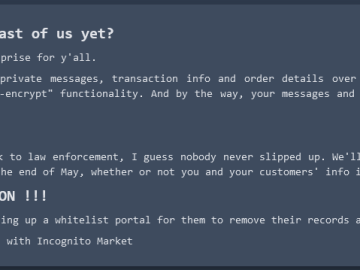
Borrowing from the playbook of ransomware purveyors, the darknet narcotics bazaar Incognito Market has begun extorting all of its vendors…
In today’s interconnected world, the threat landscape of cybersecurity is more dynamic and sophisticated than ever. Organizations face an array…
Historically speaking, Bitcoin has always made strong comebacks after each period of decline and this year’s events show that…
Deepfake technology has become a significant concern, producing computer-generated images, videos, and audio that mimic real individuals, leading to the…