Author: Cybernoz
The operators of leading open source software (OSS) package repositories, including the Python Software Foundation and the Rust Foundation, have…
Microsoft says the Russian ‘Midnight Blizzard’ hacking group recently accessed some of its internal systems and source code repositories using…
Network security professionals protect the confidentiality, integrity and availability of information across the network. They’re expert at applying strategies, processes…
Cisco addressed severe flaws in its Secure Client Pierluigi Paganini March 08, 2024 Cisco addressed two high-severity vulnerabilities in Secure…
08 Mar A Father Warns Others About The AI ‘Family Emergency Scam’ This week in cybersecurity from the editors at…
VMWare has issued secuity fixes for its VMware ESXi, Workstation, Fusion, and Cloud Foundation products. It has even taken the…
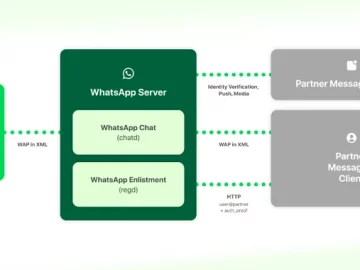
Mar 08, 2024NewsroomInteroperability / Encryption Meta has offered details on how it intends to implement interoperability in WhatsApp and Messenger…
The Massachusetts Institute of Technology’s (MITRE) Aviation Risk Identification and Assessment (ARIA) software program is a powerful tool to enhance…
JetBrains issued a warning on March 4, 2024 about two serious vulnerabilities in TeamCity server. The flaws can be used…
By Zinet Kemal, Associate Cloud Security Engineer, Best Buy The cybersecurity space, as dynamic and challenging as it is, has…
Henry Onyedikachi Echefu, a 32-year-old Nigerian national, has admitted to his role in a sophisticated business email compromise (BEC) scheme…
Cybersecurity researchers at ESET identified the cyberespionage campaign, highlighting how hackers compromised both the Tibetan news website Tibetpost and the…