Author: Cybernoz
Pwn2Own 2024 Automotive is a unique event aimed at identifying and fixing flaws in connected automotive technologies. Tokyo, Japan, hosts…
Managing cybersecurity risks in digital afterlife By Chahak Mittal, GRC Manager, Universal Logistics The concept of the digital afterlife is…
The UK’s GCHQ cyber arm, the National Cyber Security Centre (NCSC), is warning of an imminent surge in AI-based ransomware…
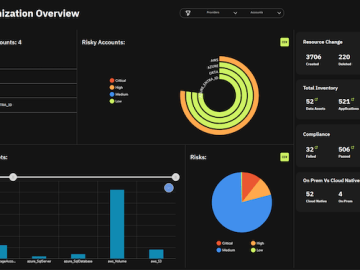
Stack Identity has unveiled the expansion of the Identity Access Risk Management Platform with identity threat detection and response (ITDR)…
Stalkers can use all kinds of apps, gadgets, devices, and phones to spy on their targets, which are often their…
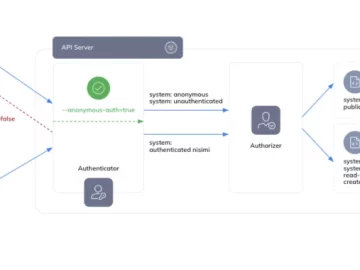
Jan 24, 2024NewsroomCloud Security / Kubernetes Cybersecurity researchers have discovered a loophole impacting Google Kubernetes Engine (GKE) that could be…
IT contractors are among the freelance workers calling on the government to consider scrapping the controversial IR35 off-payroll working rules…
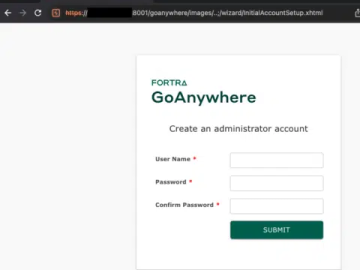
Experts released PoC exploit for Fortra GoAnywhere MFT flaw CVE-2024-0204 Pierluigi Paganini January 24, 2024 Researchers released PoC exploit code…
Security researchers hacked a Tesla Modem and collected awards of $722,500 on the first day of Pwn2Own Automotive 2024 for…
Recently, QuoIntelligence’s research team unearthed a previously undetected variant of the notorious WIREFIRE web shell, a Python-based implant targeting compromised…
An infinite variety of attack methods require customizable solutions. By Sean Newman, VP/Product Management, Corero Sun Tzu was an exceptional…
Two malicious npm packages were discovered on the npm open source package manager, which leverages GitHub to store stolen Base64-encrypted…