Author: Cybernoz
MITRE now offers an open-source version of its Aviation Risk Identification and Assessment (ARIA) software suite, OpenARIA. This initiative is…
Here’s a look at the most interesting products from the past week, featuring releases from Check Point, Delinea, Pentera, and…
Company Open Sources FHE Libraries to Build Privacy-Preserving Blockchain and AI Applications for the First Time. An investment has been…
Company Open Sources FHE Libraries to Build Privacy-Preserving Blockchain and AI Applications for the First Time. An investment has been…
TA4903 is a financially motivated cybercriminal threat actor who impersonates both US government institutions and private businesses across a wide…
Government bodies are clamping down heavily on institutions and organizations that handle sensitive customer data. For APIs, tokens are used…
Australian universities, institutes and colleges providing higher education will be asked by the government for a “detailed” and “credible” action…
The NSA and the Cybersecurity and Infrastructure Security Agency (CISA) have released five joint cybersecurity bulletins containing on best practices…
Energy Queensland, the state’s government-owned electricity generator, distributor and retailer, is seeking a chief information officer (CIO). The $30 billion…
LinkedIn has for the first time disclosed sales for its premium subscription business, saying the unit hit US$1.7 billion ($2.57…
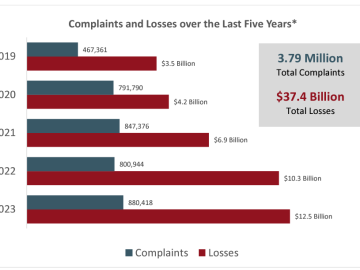
2023 FBI Internet Crime Report reported cybercrime losses reached $12.5 billion in 2023 Pierluigi Paganini March 07, 2024 The FBI…
Update: Title updated to clarify this is phishing attack conducted using a Flipper Zero. An easy phishing attack using a…