Author: Cybernoz
Apple has released a security update for iOS and iPadOS to patch two zero-day vulnerabilities which are reported to already…
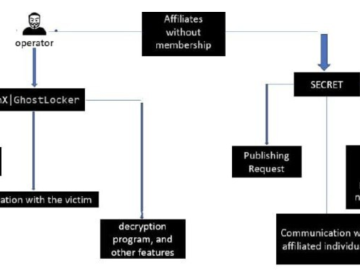
Watch out, GhostSec and Stourmous groups jointly conducting ransomware attacks Pierluigi Paganini March 06, 2024 Researchers warn that the cybercrime…
Two new zero-day vulnerabilities have been discovered in iOS and iPadOS 17.4 versions that could allow threat actors to bypass…
A critical vulnerability in OpenNMS, a widely used network monitoring solution, has been identified, allowing attackers to inject malicious JavaScript…
With each new cloud application or third-party SaaS account, the external attack surface of pretty much every organization keeps growing…
An in-depth look into a proactive website security solution that continuously detects, prioritizes, and validates web threats, helping to mitigate…
Hackers are targeting misconfigured servers running Apache Hadoop YARN, Docker, Confluence, or Redis with new Golang-based malware that automates the…
Cloudflare has announced the launch of a new firewall specifically designed to protect AI models. This pioneering initiative aims to…
American Express has recently notified its customers of a data breach involving a third-party service provider, marking a security incident…
Linux Users Beware: “Spinning YARN” Malware Campaign Targets Misconfigured Servers Running on Apache Hadoop YARN, Docker, Confluence and Redis. Cado…
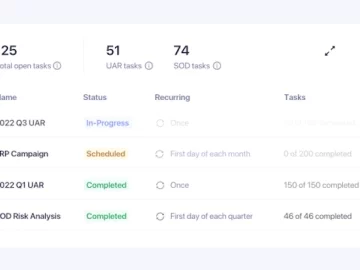
Pathlock intorduced its SAP application and data security product suite, Cybersecurity Application Controls (CAC). The release is part of Pathlock’s…
Mar 06, 2024NewsroomCyber Attack / Malware A financial entity in Vietnam was the target of a previously undocumented threat actor…