Author: Cybernoz
Hackers have been found exploiting a vulnerability in a WordPress Plugin 3DPrint Lite(CVE-2021-4436) to deploy the notorious Godzilla Web Shell….
In today’s interconnected world, maintaining a pristine digital reputation is paramount. Whether you’re an individual, a business, or an organization,…
API integrations often handle sensitive data, such as employees’ personally identifiable information (PII), companies’ financial information, or even clients’ payment…
Mar 06, 2024NewsroomVulnerability / Zero Day Apple has released security updates to address several security flaws, including two vulnerabilities that…
In an age where digital threats loom large and cyberattacks continue to proliferate, the resilience of a nation’s cybersecurity infrastructure…
Vodafone Egypt, the largest mobile operator in the country serving over 40 million customers, finds itself grappling with a partial…
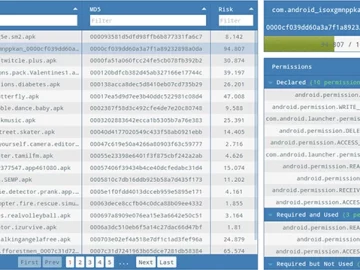
RiskInDroid (Risk Index for Android) is an open-source tool for quantitative risk analysis of Android applications based on machine learning…
Your success as an organization, especially in the cyber realm, depends on your security posture. To account for the ongoing…
Ivanti has updated its integrity checker, after the US Cyber and Infrastructure Security Agency (CISA) warned that some attackers might…
Mental framing can be powerful. Framing is the way you percieve a situation and the story you tell yourself about…
The North Korean APT hacking group Kimsuky is exploiting ScreenConnect flaws, particularly CVE-2024-1708 and CVE-2024-1709, to infect targets with a…
Airservices Australia has taken the next step in its four-year-old project to create an air traffic management system for drones,…