Author: Cybernoz
Security researcher HaxRob discovered a previously unknown Linux backdoor named GTPDOOR, designed for covert operations within mobile carrier networks. The…
Python Risk Identification Tool (PyRIT) is Microsoft’s open-source automation framework that enables security professionals and machine learning engineers to find…
LockBit ransomware group has resurfaced with claims of adding eight new victims to their dark web portal. Among the targeted…
The NoName ransomware group has claimed responsibility for targeting multiple websites in Denmark, including prominent entities such as Movia, Din…
TPG Telecom has told a senate committee that real-time sharing of natural disaster information would deliver better telecoms resilience than…
More than 95% of responding IT and security professionals believe social engineering attacks have become more sophisticated in the last…
U.S. cybersecurity and intelligence agencies have warned of Phobos ransomware attacks targeting government and critical infrastructure entities, outlining the various…
MQ Health, operator of a Macquarie University-owned teaching hospital and clinics, is recruiting an IT director, taking over from Jonathan…
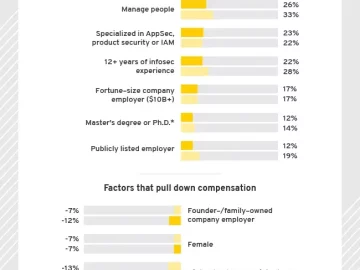
For several years, cybersecurity leaders have grappled with talent shortages in crucial cyber roles. In the face of escalating financial…
Nvidia chief executive Jensen Huang on Friday said that artificial general intelligence could – by some definitions – arrive in…
SolarWinds cyberattack was one of the largest attacks of the century in which attackers used the Golden SAML attack in…
The World Trade Organization’s moratorium on customs duties on digital transmissions, a key pillar of internet development for decades, has…