Author: Cybernoz
The Ann & Robert H. Lurie Children’s Hospital of Chicago was recently hit by a highly advanced ransomware attack, underlining…
Companies more than ever view GRC (Governance, Risk, and Compliance) as a holistic process and are taking steps toward getting…
Feb 28, 2024NewsroomPhishing Attack / Malware Mexican users have been targeted with tax-themed phishing lures at least since November 2023…
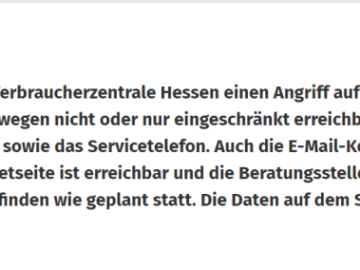
The ALPHV/BlackCat ransomware group has purportedly claimed two new victims: Verbraucherzentrale Hessen, a consumer advice center in Germany, and Electro…
Security agencies led by the FBI, the National Security Agency, and the US Cyber Command are warning that state-sponsored Russian…
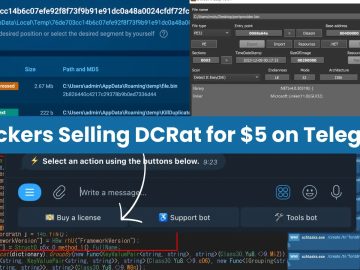
Recently, the cybersecurity researchers at ANY.RUN identified that hackers are selling DCRat subscriptions for $5 on the Telegram groups. Hackers…
Cybersecurity experts have raised alarms over a new threat vector targeting Python developers: typo-squatting on the Python Package Index (PyPI)….
Amidst growing concerns over cyber warfare, reports have surfaced regarding Russia’s advancements in artificial intelligence (AI) for spreading misinformation. Under…
88% of cybersecurity professionals believe that AI will significantly impact their jobs, now or in the near future, and 35%…
Cencora Inc. has encountered a significant cybersecurity setback, as disclosed in a recent SEC filing. Uncovered on February 21, 2024,…
Optus is laying off nearly 200 staff following the outcome of an internal review. The telco said in a statement…
In recent years, cloud migration has emerged as a pivotal strategy for organizations seeking to modernize their IT infrastructure, enhance…