Author: Cybernoz
Protecting Australia from public safety and security threats always presents a formidable challenge. Apart from our giant landmass, which means…
HackerGPT is a cutting-edge AI tool designed explicitly for the cybersecurity sector, particularly beneficial for individuals involved in ethical hacking,…
Primary school systems handle sensitive data concerning minors, while higher education institutions must safeguard intellectual property data, making them prime…
Dell has begun working to patch a late-2023 critical vulnerability in Apache Struts 2, which has been inherited by a…
The FBI’s takedown of the LockBit ransomware group last week came as LockBit was preparing to release sensitive data stolen…
Optus expects to save as much as 26 percent of the energy consumed by its radio access network, after deploying…
Military intelligence veteran Michelle McGuinness has been appointed national cyber security coordinator by the Department of Home Affairs. Home Affairs’…
Aussie Broadband has made a conditional play for fellow retail service provider Superloop, buying 19.9 percent of shares in the…
By Ron Kerbs, CEO, Kidas In the ever-evolving landscape of cyberspace, 2023 unveiled a concerning trend: major players in the…
Victoria University is on the hunt for a new chief information security officer following an initiative to converge its campus…
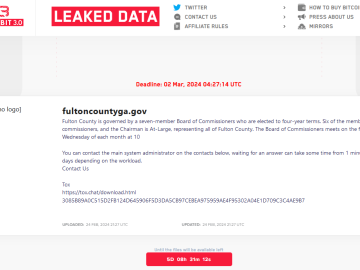
The LockBit gang is relaunching its ransomware operation on a new infrastructure less than a week after law enforcement hacked…
By Kevin Kelly, CEO and Chairman, Arcfield As the role of satellite communication systems in geopolitical conflicts and critical infrastructure…