Author: Cybernoz
The Cybersecurity and Infrastructure Security Agency said it remains firmly committed to supporting and further enhancing the Common Vulnerabilities and…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning of hackers exploiting a critical remote code execution flaw in DELMIA…
New AI-powered penetration testing framework Villager combines Kali Linux toolsets with DeepSeek AI models to fully automate cyber attack workflows….
New SEO poisoning campaign exposed! FortiGuard Labs reveals how attackers trick users with fake websites to deliver Hiddengh0st and Winos…
Browsers like Chrome, Edge, and Firefox are our traditional gateway to the internet. But lately, we have seen a new…
Sep 12, 2025Ravie Lakshmanan Apple has notified users in France of a spyware campaign targeting their devices, according to the…
The European Union (EU) Data Act comes into force today (12 September 2025), giving, says the European Commission, citizens control…
The US cybersecurity agency CISA believes that expanded partnerships, government sponsorships, transparency, modernization, and better vulnerability data quality are the…
The notorious APT-C-24 threat actor group, commonly known as Sidewinder or Rattlesnake, has evolved its attack methodology by deploying sophisticated…
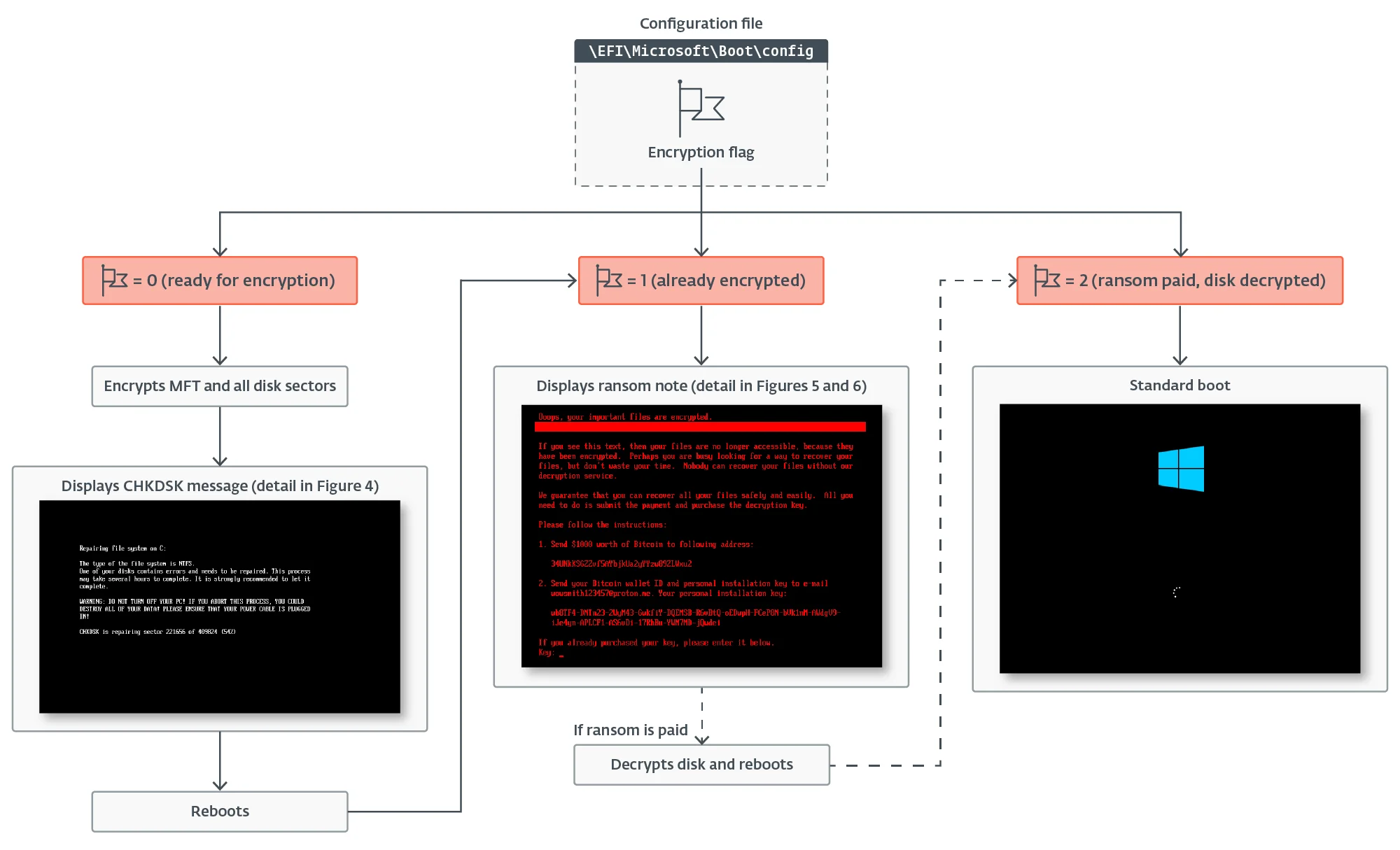
ESET researchers have discovered HybridPetya, a bootkit-and-ransomware combo that’s a copycat of the infamous Petya/NotPetya malware, augmented with the capability…
We hear so often about people falling for scams and losing money. But we often don’t find out the real…
Sep 12, 2025Ravie LakshmananVulnerability / Mobile Security Samsung has released its monthly security updates for Android, including a fix for…