Author: Cybernoz
A group of 20 tech companies have agreed to work together to prevent deceptive artificial-intelligence content from interfering with elections…
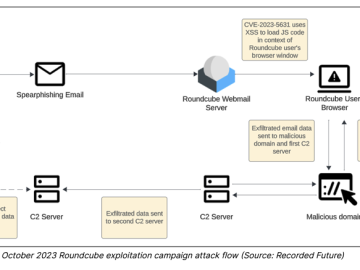
Russia-linked APT TAG-70 targets European government and military mail servers exploiting Roundcube XSS Pierluigi Paganini February 19, 2024 An APT…
Security testing for eCommerce websites has become indispensable for online retailers, as it plays a vital role in safeguarding customer…
The Anatsa banking trojan has been targeting users in Europe by infecting Android devices through malware droppers hosted on Google…
A recent analysis of the GL-AX1800 router by researchers revealed the presence of several security vulnerabilities that attackers could exploit…
Threat actors exploit Cisco AnyConnect vulnerabilities to gain unauthorized access to networks, compromise sensitive information, and potentially execute malicious activities. …
In this exploration, we delve into the multifaceted layers of Ethereum’s meteoric rise, dissecting the technological breakthroughs, the vibrant community…
SolarWinds has released updates for Access Rights Manager (ARM) and (Orion) Platform that fix vulnerabilities that could allow attackers to…
Did you know that Network Detection and Response (NDR) has become the most effective technology to detect cyber threats? In…
The Post Office’s second controversial accounting system, known as Capture, was developed in-house in the early 1990s. Following the explosion…
A massive data breach originating from a private industry contractor of the Chinese Ministry of Public Security (MPS), known as…
More than 100 Afghan websites have been suspended after a French internet services firm failed to make payments to the…