Author: Cybernoz
Software supply chain attacks have emerged as a serious threat in the rapidly evolving field of cybersecurity, especially in medical…
The manhunt for the shooter who killed conservative activist Charlie Kirk ended Friday with a suspect taken into custody, authorities…
A sophisticated malvertising campaign has been uncovered targeting unsuspecting users through “dangling commits” in a legitimate GitHub repository. Attackers are…
SecurityWeek’s cybersecurity news roundup provides a concise compilation of noteworthy stories that might have slipped under the radar. We provide…
Cisco fixes high-severity IOS XR flaws enabling image bypass and DoS Pierluigi Paganini September 12, 2025 Cisco addressed multiple high-severity…
The moment a cyberattack strikes, the clock starts ticking. Files lock up, systems stall, phones light up and the pressure…
Samsung has released its September 2025 security update, addressing a critical zero-day vulnerability that is being actively exploited in the…
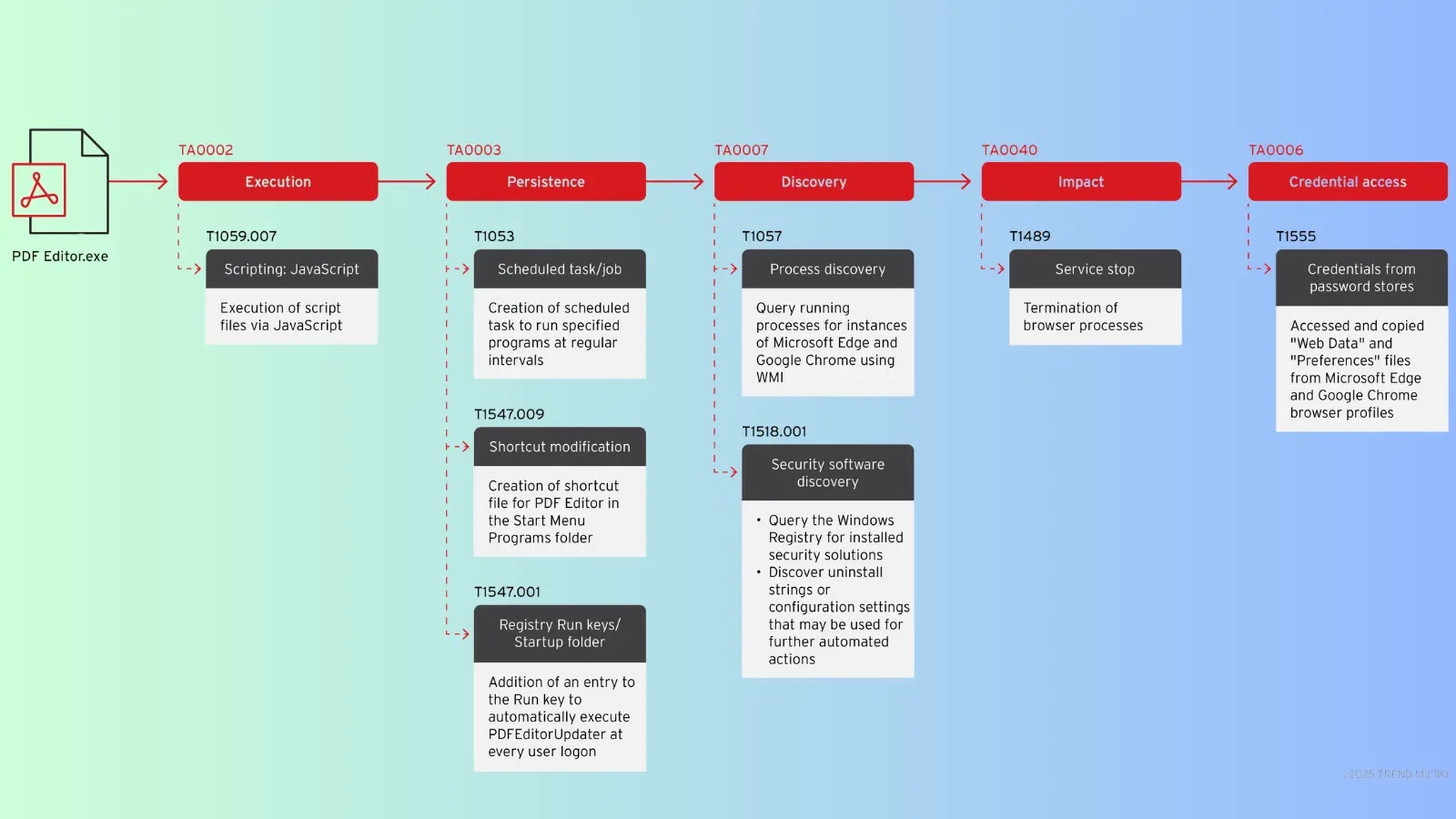
EvilAI, a new malware family tracked by Trend Research, has emerged in recent weeks disguised as legitimate AI-driven utilities. These…
Debojyoti ‘Debo’ Dutta admits that his deep domain experience means he is just “a little biased” when it comes to…
Apple in early September sent a fresh wave of threat notifications to French users it believes might have been targeted…
WebAssembly is a low-level assembly language that can process binary formats on the web. It runs on the web but…
Within mere hours of its public unveiling, the K2 Think model experienced a critical compromise that has sent ripples throughout…