Author: Cybernoz
Considering that 2024 is a historic year for elections – with an estimated half of the world’s population taking part…
Feb 16, 2024NewsroomCybersecurity / Data Breach The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has revealed that an unnamed state…
In the late 1990s, the outcome of a battle between two factions within the Post Office triggered the IT problems…
Washington County recently faced a cyberattack by Russian hackers targeting the government and courthouse. To swiftly halt the attack and…
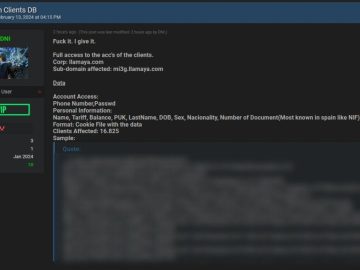
Llamaya, a prominent mobile telephony company operating under the MASMOVIL Group in Spain, has reportedly fallen victim to a massive…
Russia-linked Turla APT uses new TinyTurla-NG backdoor to spy on Polish NGOs Pierluigi Paganini February 16, 2024 Russia-linked APT group…
Security researchers Mathy Vanhoef and Héloïse Gollier, have recently uncovered several critical vulnerabilities in the Wi-Fi authentication protocols used in…
Outlook has been discovered to have an interesting vulnerability while handling specific hyperlinks, which was found to be exploited by…
The Department of State, in its ongoing efforts to combat cybercrime, has announced a $10 million reward for information leading…
Here’s a look at the most interesting products from the past week, featuring releases from Appdome, Center for Internet Security,…
Feb 16, 2024NewsroomBotnet / Network Security The U.S. government on Thursday said it disrupted a botnet comprising hundreds of small…
Imagine a cascading blackout, disrupted pipelines, or manipulated manufacturing processes – all orchestrated through a cyberattack. This chilling reality paints…