Author: Cybernoz
The SEC is tightening its focus on financial data breach response mechanisms of very specific set of financial institutions, with…
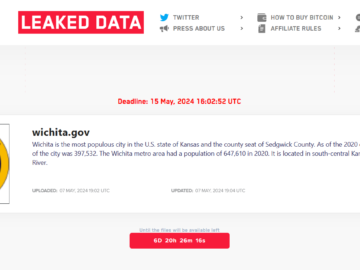
City of Wichita disclosed a data breach after the recent ransomware attack Pierluigi Paganini May 17, 2024 The City of…
Malware experts all over the world can’t do their jobs without YARA. YARA has been updated many times to add…
17 May Cybersecurity Tips For Small Businesses: 7 Ways To Protect Your Company Posted at 08:53h in Blogs by Di…
A new report from XM Cyber has found – among other insights – a dramatic gap between where most organizations…
In the contemporary landscape of corporate responsibility, environmental sustainability has become a vital concern. With enterprises facing increasing regulatory pressure…
The Cybersecurity and Infrastructure Security Agency (CISA) has recently updated its known exploited vulnerabilities catalog to include three new entries,…
The email campaign impersonates the Facebook Ads Team to trick users into clicking a malicious link, as the email leverages…
ViperSoftX malware, known for stealing cryptocurrency information, now leverages Tesseract, an open-source OCR engine, to target infected systems, which extracts…
The US Justice Department had unsealed charges against a US woman and an Ukranian man who, along with three unidentified…
Following the recent Ascension ransomware attack, legal challenges are mounting for the healthcare giant. Just days after the cyberattack disrupted…
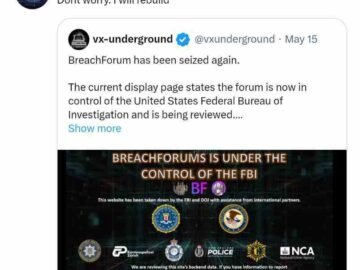
While the recent takedown of BreachForums by the FBI, in collaboration with international law enforcement agencies, marked a significant victory…