Author: Cybernoz
A Tennessee court has sentenced a Memphis man who worked for a DVD and Blu-ray manufacturing and distribution company to…
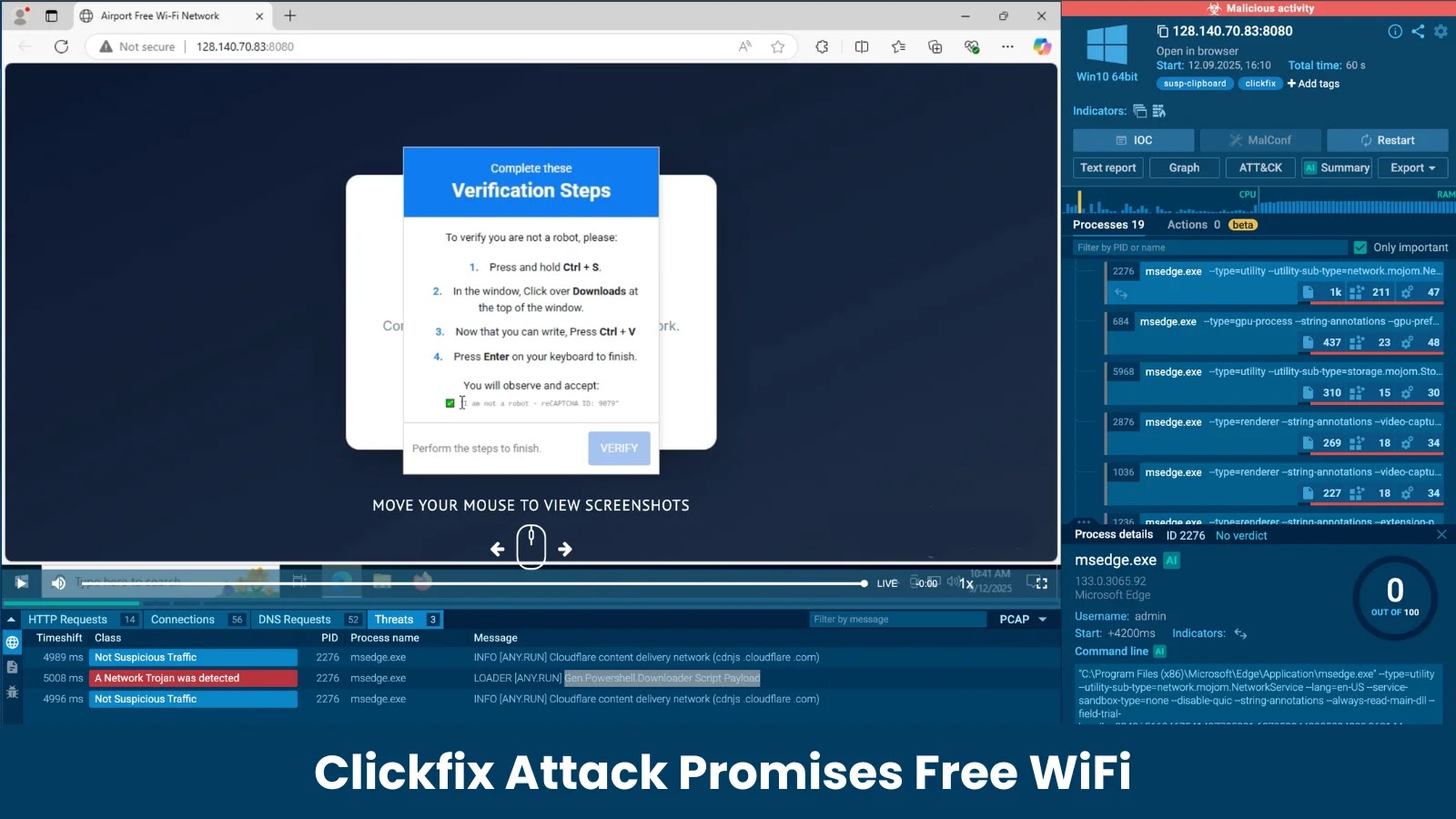
The Cybersecuritynews researcher team uncovered a sophisticated social engineering campaign that is exploiting the public’s need for free internet access,…
A sophisticated malvertising campaign has been uncovered targeting unsuspecting users through “dangling commits” in a legitimate GitHub repository. Attackers are…
A new report from Cofense reveals that cybercriminals are blending phishing and malware, including Muck Stealer, Info Stealer, ConnectWise RAT,…
The Ministry of Defence (MoD) has selected Google Cloud to provide it with sovereign cloud capabilities in a deal worth…
Cybercrime and online scams have officially overtaken traditional threats as the primary regional security concern for the Association of Southeast…
A critical security vulnerability has been discovered in the popular Axios HTTP client library that allows attackers to crash Node.js…
Backdoor malware is a covert type of malicious software designed to bypass standard authentication mechanisms and provide persistent, unauthorized access…
Cloud block storage allows organisations to run applications that depend on high throughput and low latency in the cloud. The…
UK train operator LNER (London North Eastern Railway) discloses a data breach Pierluigi Paganini September 12, 2025 LNER warns of…
Samsung has patched a remote code execution vulnerability that was exploited in zero-day attacks targeting its Android devices. Tracked as…
A new, sophisticated malware campaign has been uncovered that leverages Microsoft’s Azure Functions for its command-and-control (C2) infrastructure, a novel…