Author: Cybernoz
Over the next few years, the number of organizations navigating to the cloud to advance their business goals is expected…
February 2, 2024 – CISA has ordered all FCEB agencies to disconnect all instances of Ivanti Connect Secure and Ivanti…
Feb 05, 2024NewsroomSpyware / Surveillance The iPhones belonging to nearly three dozen journalists, activists, human rights lawyers, and civil society…
IT security leaders are recognising the risks and opportunities of generative artificial intelligence (GenAI) for enterprise IT. In April 2023,…
The impact of the massive Okta data breach lingers, continuing to provide an opportunistic terrain for hackers. Cloudflare, a prominent…
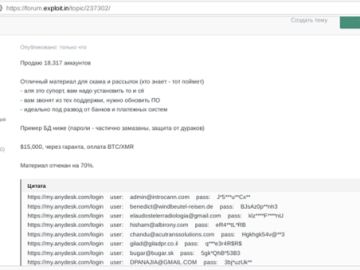
Software firm AnyDesk disclosed a security breach Pierluigi Paganini February 05, 2024 Remote desktop software company AnyDesk announced that threat…
AnyDesk, a widely-used platform for remote access software, fell victim to a ransomware attack, exposing its source code and private…
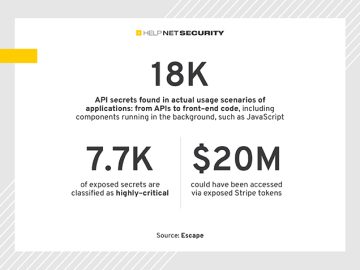
Escape’s security research team scanned 189.5 million URLs and found more than 18,000 exposed API secrets. 41% of exposed secrets…
A recent malware campaign dubbed “Commando Cat” has set its sights on exposed Docker API endpoints, posing a significant threat…
A new large-scale campaign named “ApateWeb ” has been discovered, which uses over 130,000 domains to deliver scareware, potentially unwanted…
In the realm of cybersecurity, understanding the nuances between hashing, salting, and encryption is crucial for safeguarding sensitive data. Each…
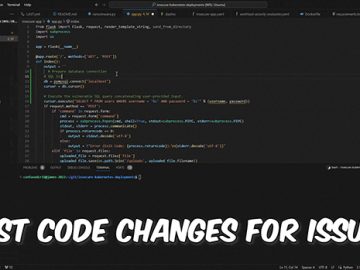
Latio Application Security Tester is an open-source tool that enables the usage of OpenAI to scan code from the CLI…