Author: Cybernoz
London North Eastern Railway (LNER) has confirmed that an unauthorized breach at one of its third-party suppliers exposed contact details…
US Senator Ron Wyden urges the FTC to investigate Microsoft after its software contributed to a major ransomware attack on…
Microsoft Teams will automatically alert users when they send or receive a private message containing links that are tagged as…
A novel speculative execution attack named VMSCAPE allows a malicious virtual machine (VM) to breach its security boundaries and steal…
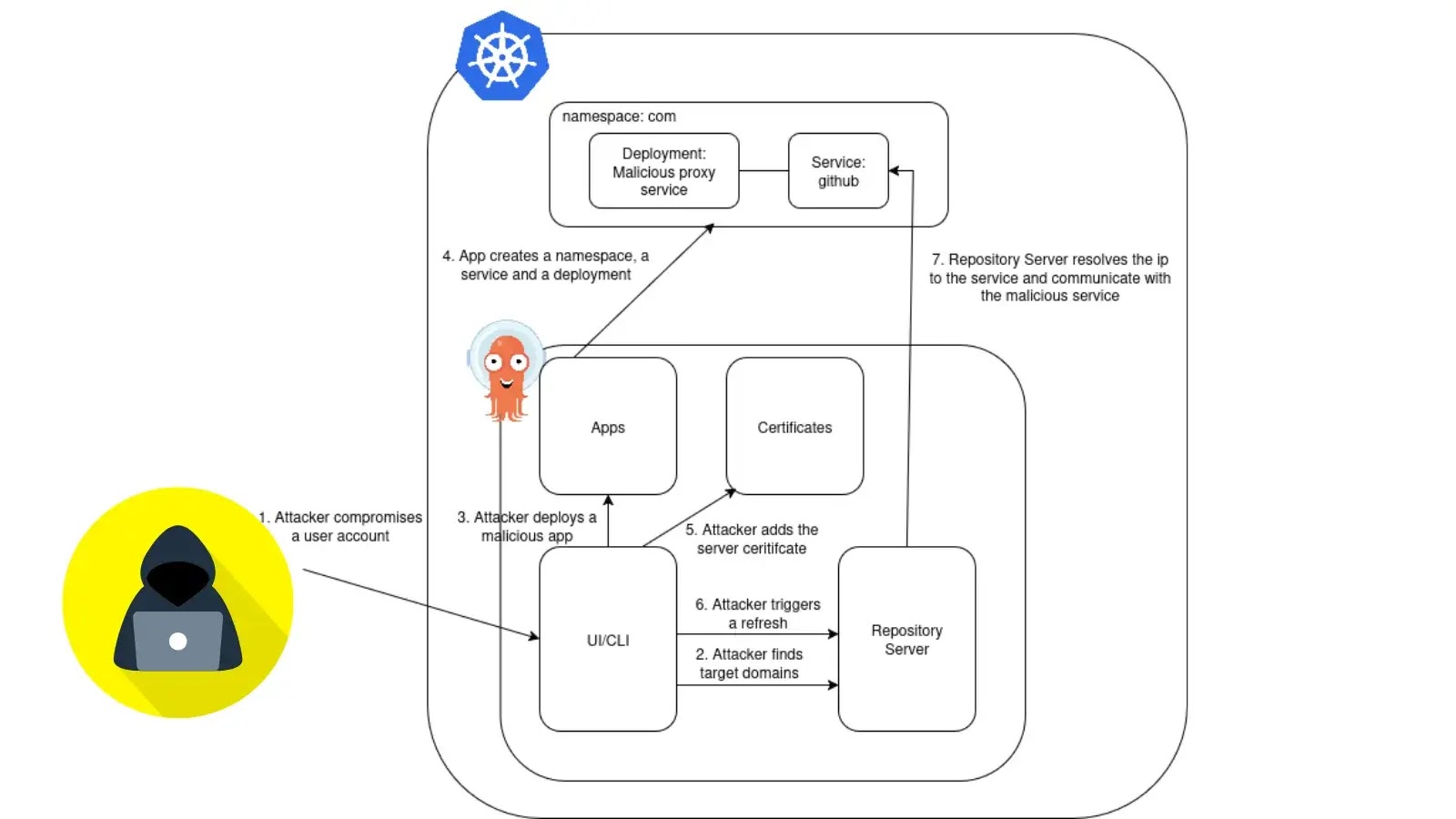
A newly discovered attack method targeting ArgoCD and Kubernetes that could give red-teamers fresh ammo and blue-teamers fresh headaches. This…
U.S. Senator Ron Wyden has called on the Federal Trade Commission (FTC) to probe Microsoft and hold it responsible for…
The Akira ransomware gang is actively exploiting CVE-2024-40766, a year-old critical-severity access control vulnerability, to gain unauthorized access to SonicWall devices. The…
Cyber attackers constantly refine their evasion methods. That’s what makes threats, including phishing, increasingly hard to detect and investigate. Kits…
Sep 11, 2025Ravie LakshmananArtificial Intelligence / Mobile Security Google on Tuesday announced that its new Google Pixel 10 phones support…
Law enforcement experts and policymakers are due to meet on 12 September to decide on proposals to require technology companies,…
A new Spectre-like attack dubbed VMScape allows a malicious virtual machine (VM) to leak cryptographic keys from an unmodified QEMU…
In early May 2025, security teams began observing a sudden rise in post-exploitation activity leveraging an open-source command-and-control framework known…