Author: Cybernoz
Despite reported threat detection, investigation, and response (TDIR) improvements in security operations, more than half of organizations still experienced significant…
China-linked APT deployed malware in a network of the Dutch Ministry of Defence Pierluigi Paganini February 07, 2024 China-linked APT group breached the Dutch…
DDoS Attack via Compromised Smart Toothbrushes Disrupts Swiss Company’s Network A Swiss company recently faced a significant setback due to…
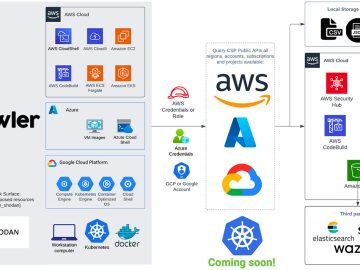
Prowler is an open-source security tool designed to assess, audit, and enhance the security of AWS, GCP, and Azure. It’s…
Feb 07, 2024NewsroomCyber Espionage / Network Security Chinese state-backed hackers broke into a computer network that’s used by the Dutch…
Verizon, one of the largest telecommunication giants in the United States, finds itself embroiled in yet another data breach saga,…
Aussie Broadband’s $262 million acquisition of unified communications-as-a-service provider Symbio moved a step closer, with Symbio shareholders voting in favour…
The allocation of budget for cybersecurity holds paramount importance in the modern digital landscape. In an era where cyber threats…
According to recent surveys, 98% of organizations keep their financial, business, customer and/or employee information in the cloud but, at…
Feb 07, 2024NewsroomCybersecurity / Software Security JetBrains is alerting customers of a critical security flaw in its TeamCity On-Premises continuous…
In response to a recent cyberattack on AnyDesk, a prominent provider of remote desktop software, has issued a comprehensive statement…
With the highly anticipated season nine of the Pakistan Super League (PSL) just around the corner, organizers and fans have…