Author: Cybernoz
Sep 11, 2025Ravie LakshmananMalvertising / Browser Security Cybersecurity researchers have disclosed two new campaigns that are serving fake browser extensions…
Attackers abuse ConnectWise ScreenConnect to drop AsyncRAT Pierluigi Paganini September 11, 2025 Hackers exploit ConnectWise ScreenConnect to drop AsyncRAT via…
Spoof the email delivery platform SendGrid and employ fake Cloudflare CAPTCHA interstitials to lend legitimacy before redirecting unsuspecting users to…
U.S. Senator Ron Wyden has called on the Federal Trade Commission (FTC) to investigate Microsoft for what he terms “gross…
A critical vulnerability in NVIDIA’s NVDebug tool could allow attackers to gain elevated system access, execute code, or tamper with…
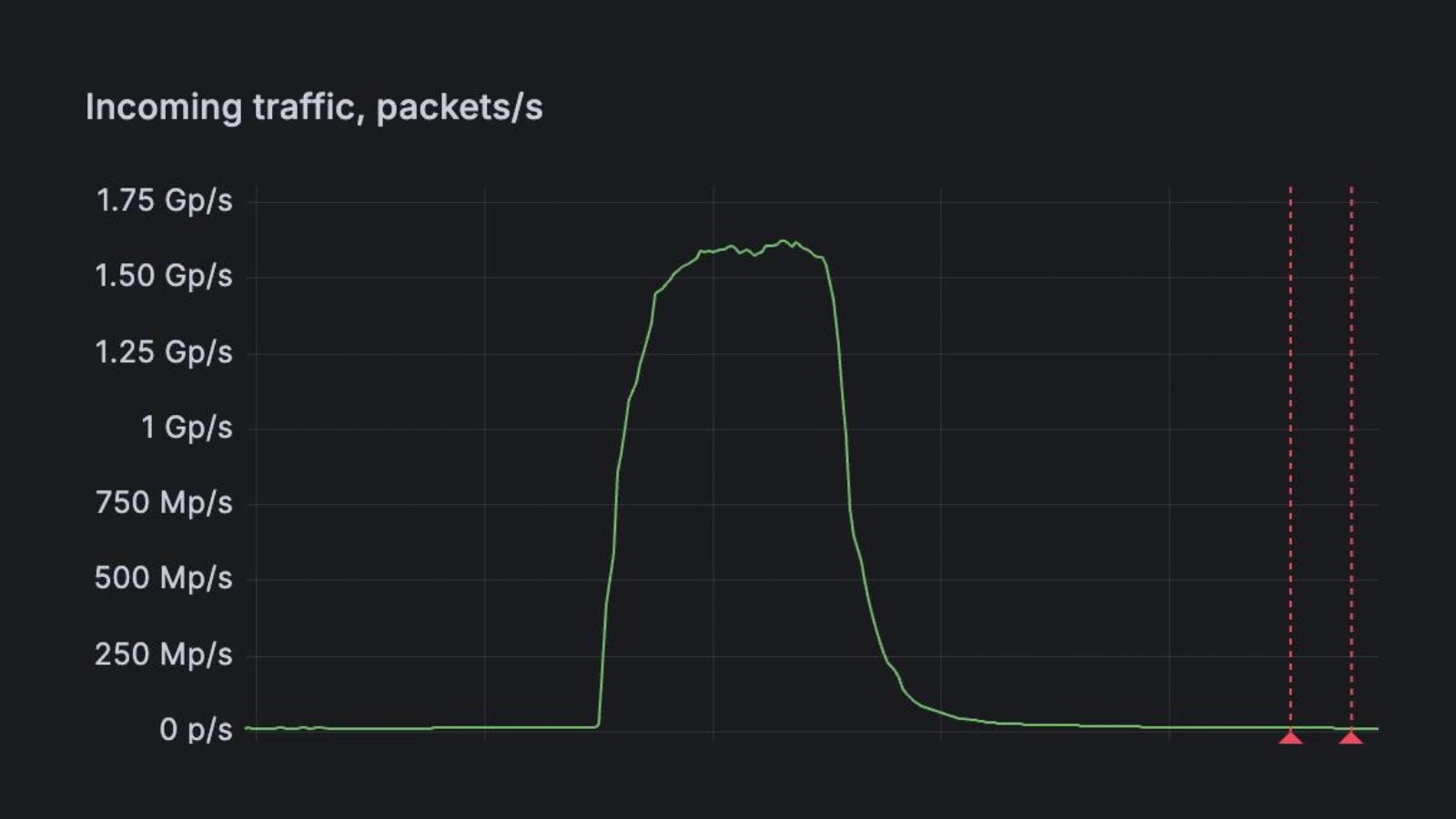
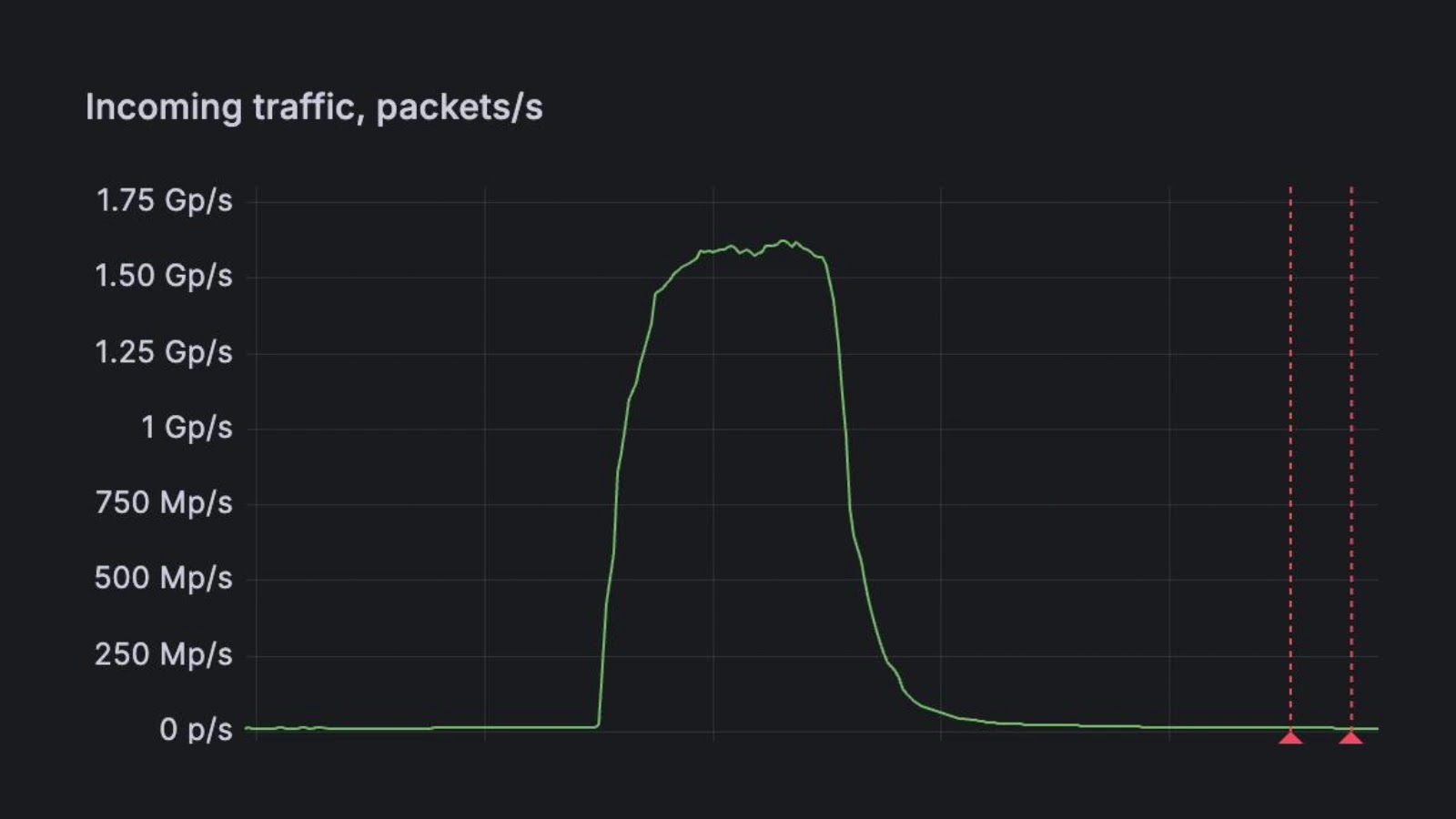
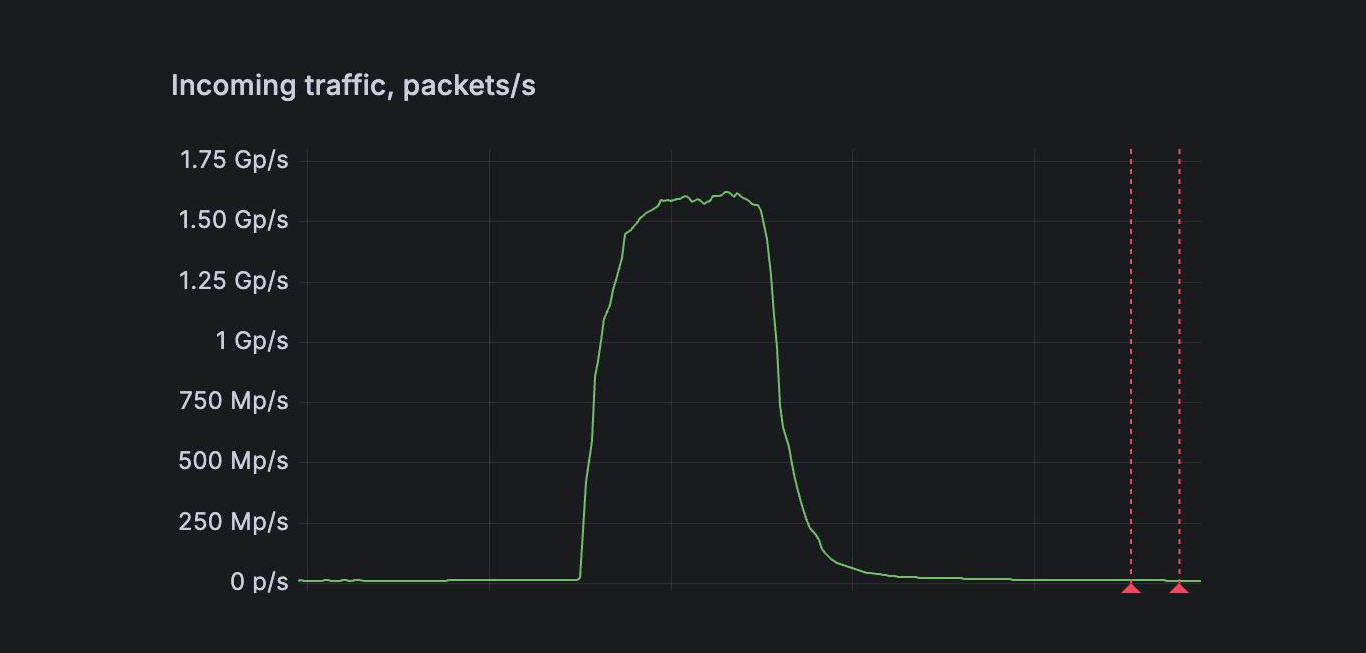
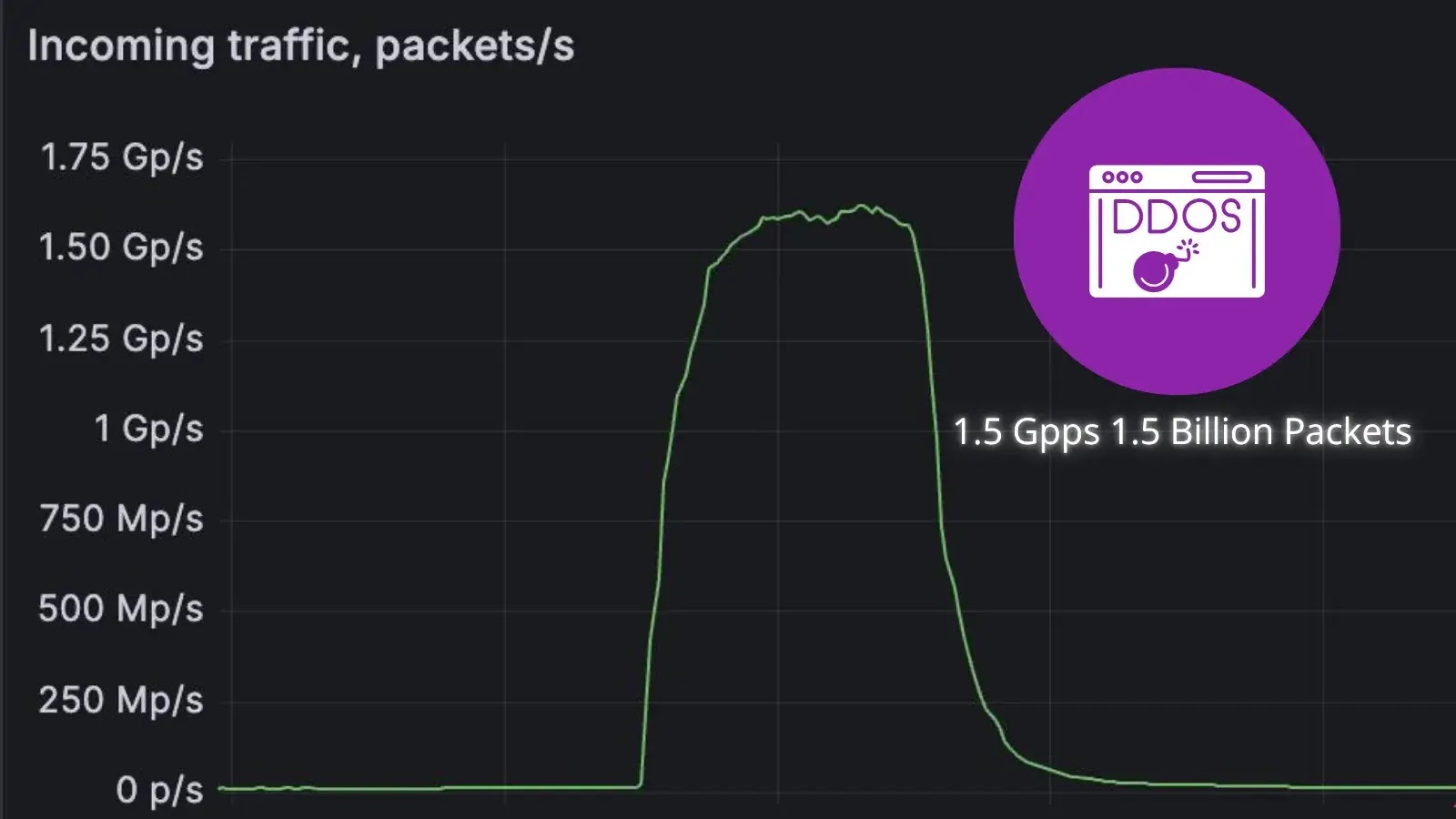
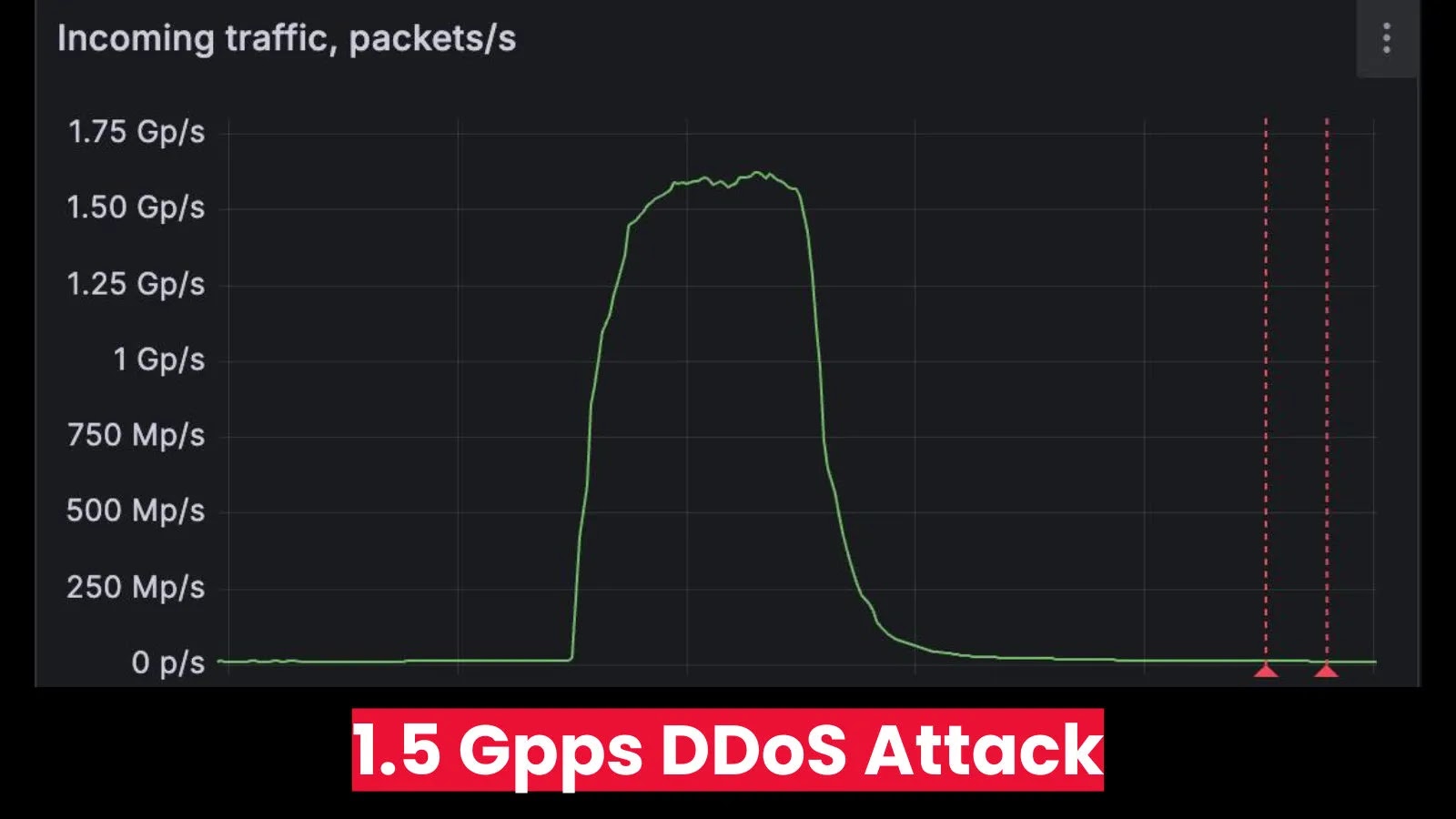
FastNetMon today announced that it detected a record-scale distributed denial-of-service (DDoS) attack targeting the website of a leading DDoS scrubbing vendor in…
FastNetMon today announced that it detected a record-scale distributed denial-of-service (DDoS) attack targeting the website of a leading DDoS scrubbing vendor in…
London, United Kingdom, September 11th, 2025, CyberNewsWire FastNetMon today announced that it detected a record-scale distributed denial-of-service (DDoS) attack targeting the website…
Jaguar Land Rover discloses a data breach after recent cyberattack Pierluigi Paganini September 11, 2025 Jaguar Land Rover confirms a…
FastNetMon today announced it detected a record-scale distributed denial-of-service (DDoS) attack targeting the website of a leading DDoS scrubbing vendor…
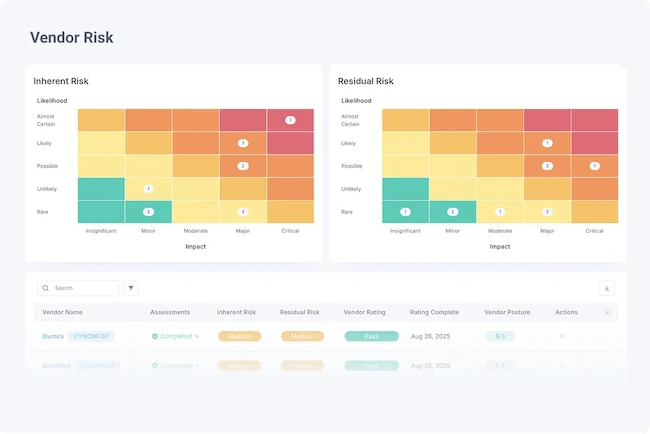
Cynomi has launched its Third-Party Risk Management (TPRM) module. Delivered as an add-on to the Cynomi vCISO Platform, the new…
FastNetMon, a prominent provider of DDoS detection solutions, announced this week that it had identified and helped mitigate a record-breaking…