Author: Cybernoz
Documents exclusively obtained by WIRED reveal that AI surveillance software tracked thousands of people using the London Underground to detect…
By 2025, Britain is set to ditch physical immigration status documents such as Biometric Residence Permits (BRPs) and Biometric Residence…
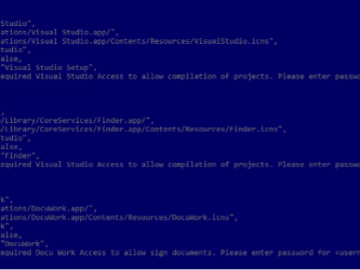
macOS Backdoor RustDoor likely linked to Alphv/BlackCat ransomware operations Pierluigi Paganini February 10, 2024 Bitdefender Researchers linked a new macOS…
By Ashish Tandon, Founder & CEO, Indusface In the ever-evolving landscape of digital threats and cyberattacks, the year 2024 demands…
by Shrikant Navelkar, Director, Clover Infotech The need for hybrid data centers is closely tied to the growing adoption of…
Feb 10, 2024NewsroommacOS Malware / Cyber Threat Apple macOS users are the target of a new Rust-based backdoor that has…
The U.S. Federal Trade Commission (FTC) says Americans lost over $10 billion to scammers in 2023, marking a 14% increase…
CISA confirmed today that attackers are actively exploiting a critical remote code execution (RCE) bug patched by Fortinet on Thursday….
The Ministry of Defence (MoD) has revealed it has expanded an existing defensive security initiative with ethical hacking and penetration…
The Canadian government plans to ban the Flipper Zero and similar devices after tagging them as tools thieves can use…
In a new blog post, Ivanti says that it has found another vulnerability and urges customers to “immediately take action…
Feb 09, 2024NewsroomMalware / Dark Web The operators of Raspberry Robin are now using two new one-day exploits to achieve…