Author: Cybernoz
By Nicole Allen, Senior Marketing Executive at Salt Communications Many organisations use WhatsApp for routine business interactions even though it…
Dynatrace announced it has extended its analytics and automation platform to provide holistic observability and security for LLMs and generative…
Feb 01, 2024NewsroomCryptocurrency / Botnet Cybersecurity researchers have detailed an updated version of the malware HeadCrab that’s known to target…
It was all change at the top for Crew Clothing in 2023 as the senior team departed. But the technology…
Multiple malware used in attacks exploiting Ivanti VPN flaws Pierluigi Paganini February 01, 2024 Mandiant spotted new malware used by…
Recently, Cluster25, a threat intelligence firm, uncovered a spear-phishing campaign dubbed “The Bear and the Shell,” specifically targeting entities critical…
Today, API security company Salt Security has announced that it has been accepted to the Amazon Web Services (AWS) Lambda Ready…
A financially motivated threat actor tracked as UNC4990 is using booby-trapped USB storage devices and malicious payloads hosted on popular…
The government is leaving it up to the statutory public inquiry into the Post Office scandal to ascertain if and…
Ransomware has been one of the top threats to organizations, contributing several millions of dollars to multiple organizations worldwide. Most…
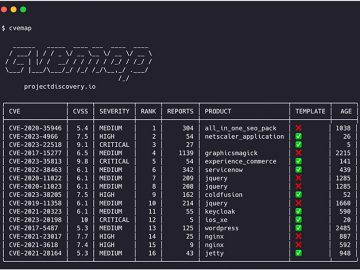
CVEMap is an open-source command-line interface (CLI) tool that allows you to explore Common Vulnerabilities and Exposures (CVEs). It’s designed…
Feb 01, 2024NewsroomNetwork Security / Malware Google-owned Mandiant said it identified new malware employed by a China-nexus espionage threat actor…