Author: Cybernoz
A new wave of macOS-targeted malware has emerged under the radar—despite employing advanced process reconnaissance and maintaining successful notarization status…
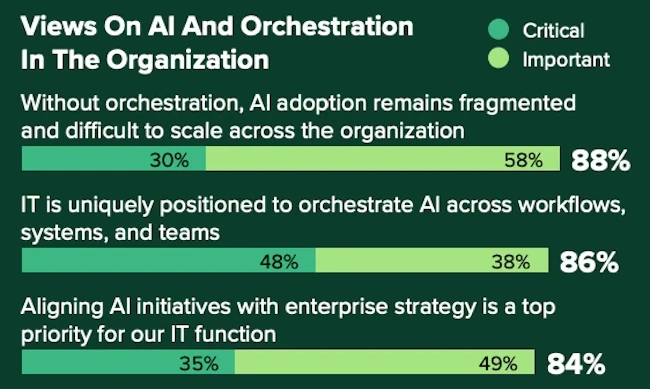
AI is being adopted across industries, but many organizations are hitting the same obstacles, according to Tines. IT leaders say…
Sep 11, 2025Ravie LakshmananMalware / Credential Theft Cybersecurity researchers have disclosed details of a new campaign that leverages ConnectWise ScreenConnect,…
The Australian Cyber Security Centre (ACSC) has issued a critical alert regarding a severe access control vulnerability in SonicWall products…
The Australian Cyber Security Centre (ACSC) has issued an urgent warning about a critical vulnerability in SonicWall firewall devices that…
You type your email address into a website form but never hit submit. Hours later, a marketing email shows up…
On September 8th, 2025, at approximately 9AM EST, the npm ecosystem faced an acute supply chain attack. A threat actor…
In this Help Net Security interview, Gregory Richardson, Vice President, Advisory CISO Worldwide, at BlackBerry, talks about the growing risks…
In this Help Net Security video, John Wilson, Senior Fellow, Threat Research at Fortra, explores the state of DMARC adoption…
Queensland Rail is four months into using SAP SuccessFactors, with the learning module “put[ting] learning back on the map” in…
To succeed in the risk environment, risk, audit, and compliance leaders need to focus on what Gartner calls “reflexive risk…
We speak with Mick Baccio, Global Security Strategist at Splunk in Boston at .conf25. Mick outlines the evolution of the…