Author: Cybernoz
The largest supply-chain compromise in the history of the NPM ecosystem has impacted roughly 10% of all cloud environments, but…
CyberVolk ransomware first emerged in May 2024, rapidly evolving into a sophisticated threat aimed at government agencies and critical infrastructure…
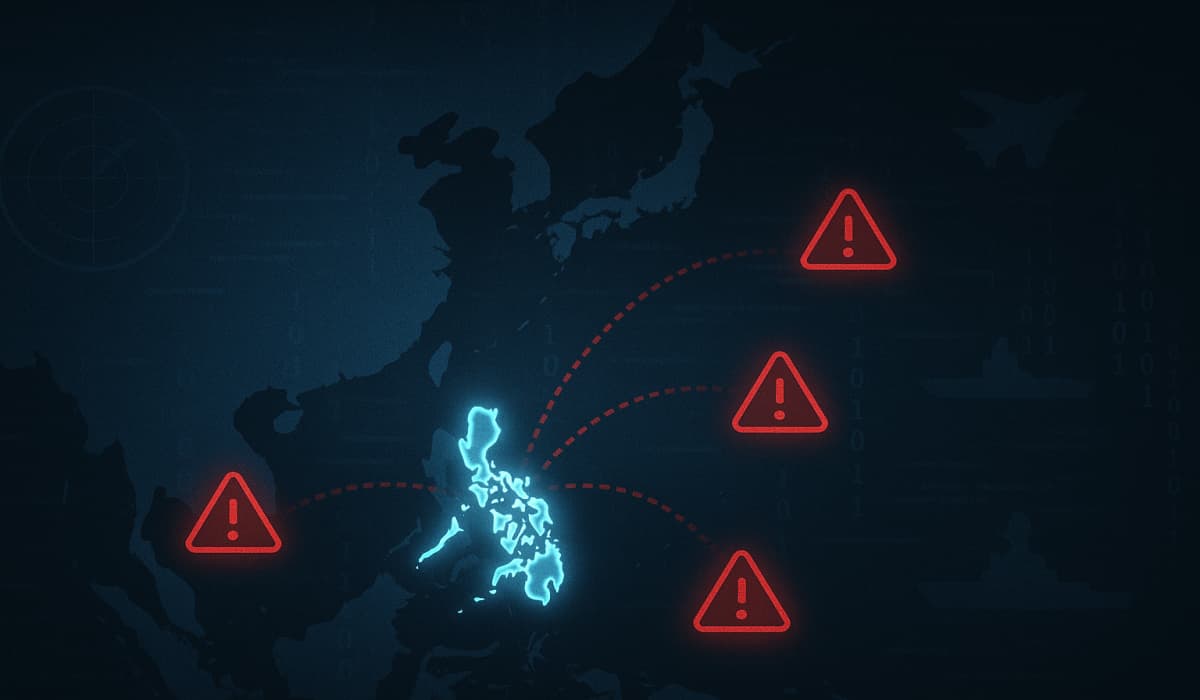
Bitdefender uncovers EggStreme, a fileless malware by a China-based APT targeting the Philippine military and APAC organisations. Cybersecurity researchers at…
Jaguar Land Rover (JLR) has revealed that a forensic investigation into the cyber attack on the company that took place…
The types of creative barriers that limit our potential There are multiple constraints that limit how creative we can be…
WASHINGTON—The senior cybersecurity official on the National Security Council said Tuesday the U.S. needs to embrace more offensive cyber capabilities…
A joint investigative sweep across three states kicked off this week aimed at identifying companies that aren’t following opt-out laws…
Google is integrating C2PA Content Credentials into the Pixel 10 camera and Google Photos, to help users distinguish between authentic,…
A remote code execution vulnerability has been discovered in the Cursor AI Code Editor, enabling a malicious code repository to…
The Amp’ed RF BT-AP 111 Bluetooth Access Point has been discovered to expose its HTTP-based administrative interface entirely without authentication…
Sep 10, 2025Ravie LakshmananCybersecurity / Malware An advanced persistent threat (APT) group from China has been attributed to the compromise…
Back in August 2023, attackers tied to the Scattered Spider group didn’t exploit a zero-day vulnerability to hack Clorox. They…