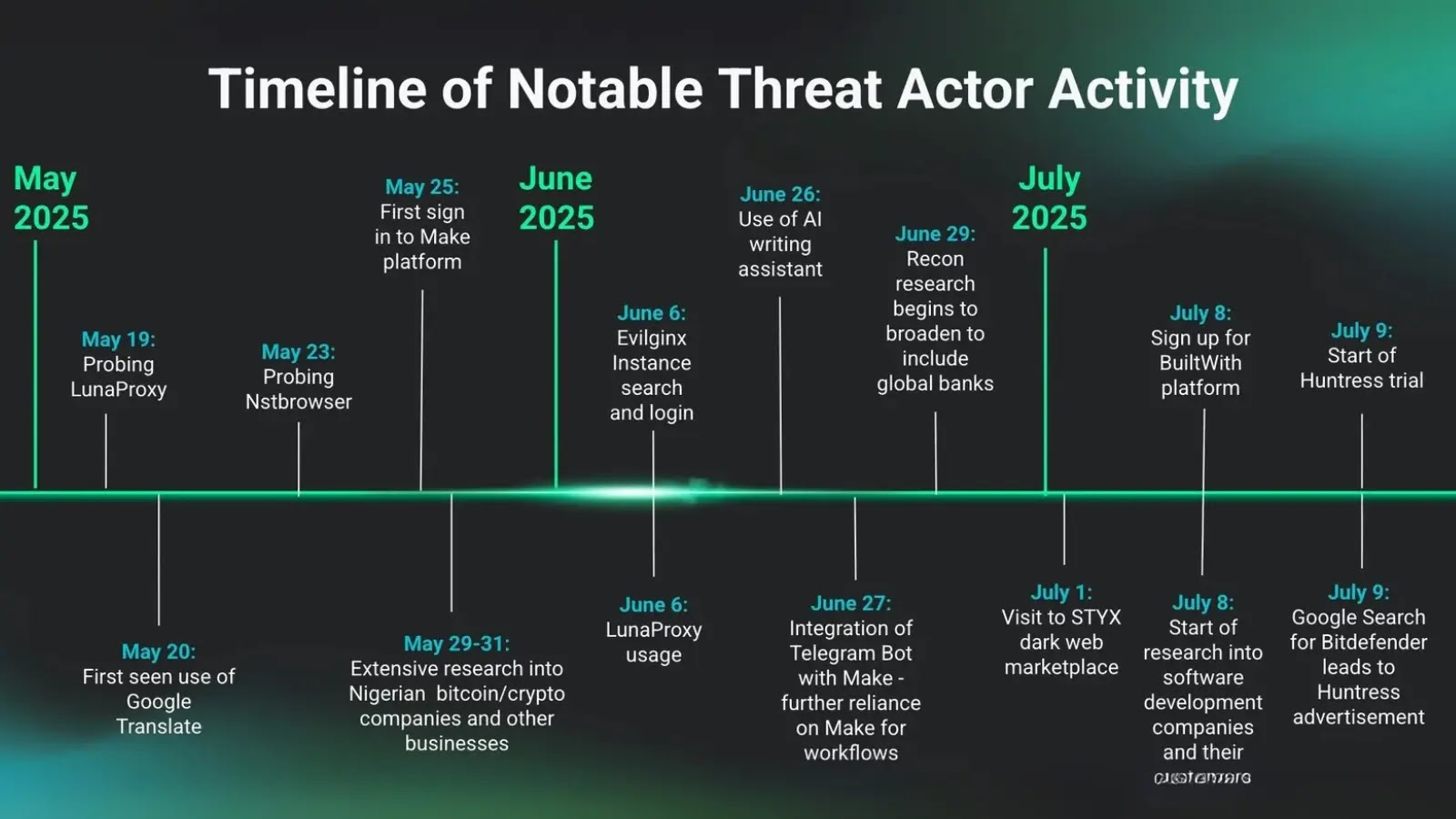
Author: Cybernoz
Apple has introduced Memory Integrity Enforcement (MIE), a system-wide security feature designed to crush one of the most persistent threats…
Given the serious financial and reputational risks of incidents that grind business to a halt, organizations need to prioritize a…
HackerOne has confirmed it was among the companies affected by a recent data breach that provided unauthorized access to its…
In a twist of fate that underscores both the power and inherent transparency of endpoint detection and response (EDR) solutions….
Sep 10, 2025The Hacker NewsMalware Analysis / Enterprise Security Phishing-as-a-Service (PhaaS) platforms keep evolving, giving attackers faster and cheaper ways…
KillSec Ransomware is Attacking Healthcare Institutions in Brazil Pierluigi Paganini September 10, 2025 KillSec Ransomware claimed responsibility for a cyberattack…
Microsoft has released patches for two significant vulnerabilities in Microsoft Office that could allow attackers to execute malicious code on…
A sophisticated espionage campaign leveraging a previously unknown malware strain dubbed GONEPOSTAL, attributed to the notorious Russian state-sponsored group KTA007,…
Microsoft Patch Tuesday security updates for September 2025 fixed two zero-day flaws Pierluigi Paganini September 10, 2025 Microsoft Patch Tuesday…
Sophos has resolved an authentication bypass vulnerability in its AP6 Series Wireless Access Points that could allow attackers to gain…
Sophos has released an important security advisory addressing a critical authentication bypass vulnerability in its AP6 Series Wireless Points. Attackers who…
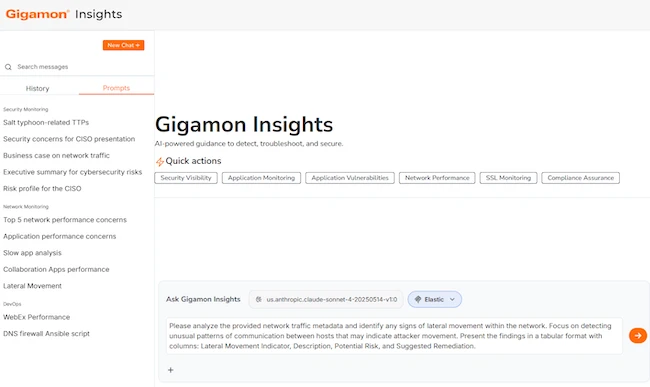
Gigamon has released Gigamon Insights, an agentic AI application purpose-built for network-derived telemetry that will deliver instant guidance for security…