Author: Cybernoz
Ransomware threat actors are spending less time on compromised networks before security solutions sound the alarm. In the first half of…
RELATED NEWS Telekopye Toolkit Unveiled: ESET research exposes a potent phishing toolkit named Telekopye, designed by Russian hackers, enabling even…
The University of Minnesota has confirmed that a threat actor has exfiltrated data from its systems, but says no malware…
Two vulnerabilities affecting some version of Jupiter X Core, a premium plugin for setting up WordPress and WooCommerce websites, allow…
Oligo Security is one of the leading open source cybersecurity platforms, pioneering the next wave of application security with a…
We’re down to the final weeks of registration for mWISE, the highly targeted, community-focused cybersecurity conference from Mandiant, now part…
At around 5:30 pm Moscow time on August 23, the Embraer Legacy 600 private business jet took to the skies….
Cybercriminals behind the Smoke Loader botnet are using a new piece of malware called Whiffy Recon to triangulate the location…
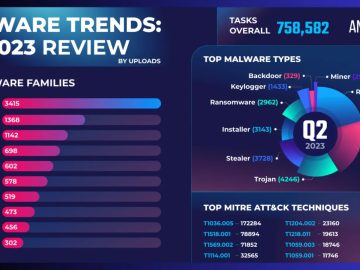
ANY.RUN, an interactive online sandbox for fast malware analysis, has published the results of its research into the top cyber…
The most widely used network protocol analyzer in the world, Wireshark, has released version 4.0.8. It is employed for network…
[ This article was originally published here ] Cybersecurity as a competitive advantage The economy is on the minds of…
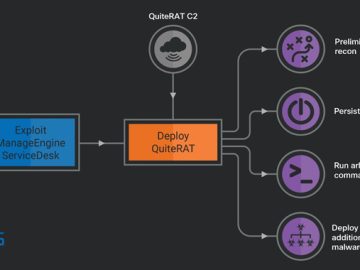
Aug 24, 2023THNCyber Attack / Hacking The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a…