Author: Cybernoz
We recently discussed the new SEC rule requiring all registered companies to report material cyber incidents within four (4) days….
Researchers at Secureworks have come across a mysterious piece of malware that scans for nearby Wi-Fi access points in an…
Proof-of-concept exploit code is now available for a critical Ivanti Sentry authentication bypass vulnerability that enables attackers to execute code…
Strategies for Preventing Data Breaches in the Translation Industry By Ofer Tirosh, CEO of Tomedes When it comes to translation,…
The UK government will be hosting an international artificial intelligence (AI) safety summit at Bletchley Park on 1 and 2…
I hope you’ve been doing well! What We’re Known For It’s long had a place in my heart, as I…
Cisco on Wednesday announced patches for six vulnerabilities in its products, including three high-severity bugs in NX-OS and FXOS software…
Call us Toll Free (USA): 1-833-844-9468 International: +1-603-280-4451 M-F 8am to 6pm EST Contact us: [email protected] Cyber Defense Magazine is…
By Craig Lurey, CTO and Co-Founder, Keeper Security As Artificial Intelligence–better known as AI–proves to be a revolutionary technology that is…
Google has moved to address some of the more pressing needs faced by users of its Workspace service, adding artificial…
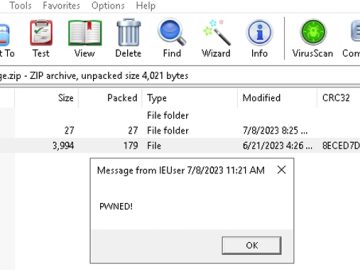
Aug 24, 2023THNEndpoint Security / Zero-Day A recently patched security flaw in the popular WinRAR archiving software has been exploited…
The number of girls choosing to take GCSE computing has risen for the second year in a row after a…





![[tl;dr sec] #196 – How Secrets Leak in CI/CD, AI Threat Modeling, Supply Chain [tl;dr sec] #196 - How Secrets Leak in CI/CD, AI Threat Modeling, Supply Chain](https://image.cybernoz.com/wp-content/uploads/2023/08/tldr-sec-196-How-Secrets-Leak-in-CICD-AI-360x270.jpg)