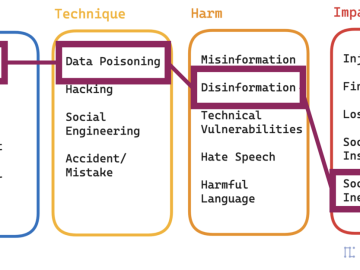
Author: Cybernoz
There is a standard playbook and best practice for when an organization discovers or is notified about a software vulnerability:…
Identity security has become increasingly vital for enterprises and large government organisations, especially in the aftermath of Covid-19. As workers…
In this Help Net Security interview, David Gugelmann, CEO at Exeon, sheds light on the current cyber threats and their…
Juniper Networks is warning of four vulnerabilities in two versions of its Junos OS operating system, which can be chained…
Retailer Adairs has outlined strategic plans to upgrade its digital customer experience, including with increased personalisation and AI trials. The…
State policing agencies are providing Services Australia with search warrants used to access password-cracking technology during investigations into welfare fraud. …
Digital investments in its fee-based businesses set insurer IAG back $37 million in the 2022-2023 financial year, leading it to…
Are you considering developing a Java web application? While you may have the skills to do it yourself, have you…
Some of the world’s biggest advertisers, from food giant Nestle to consumer goods multinational Unilever, are experimenting with using generative…
At its core, web scraping involves automatically extracting data from websites, enabling individuals and organizations to obtain valuable data for…
My whole career has been in Information Security, and I began thinking a lot about AI in 2015. Since then…
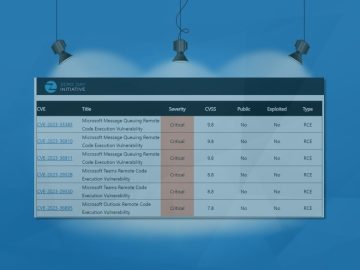
Formed by TrendMicro, the Zero Day Initiative (ZDI) was created to encourage the reporting of 0-day vulnerabilities privately to the…