Author: Cybernoz
Check Point signs a definitive agreement to acquire Perimeter 81, a Security Service Edge (SSE) company. With this acquisition, Check…
After WormGPT, a malicious artificial intelligence chatbot built on the open-source GPT-J large language model (LLM), another AI chatbot Evil-GPT…
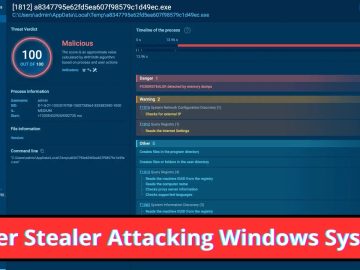
Ficker Stealer is a type of malware that steals sensitive information from over 40 browsers, including popular ones like Chrome,…
DTX brings together creative minds, technical experts and the latest tools needed to drive change and generate value across today’s…
Infostealer malware is becoming extremely popular among cybercriminals, especially in the malware-as-a-service (MaaS) based sector. These kinds of malware remain…
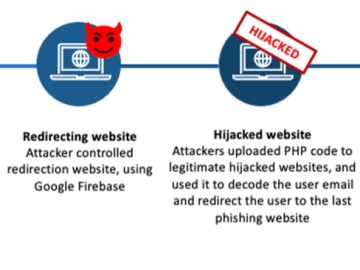
A phishing campaign leveraging the EvilProxy phishing-as-a-service (PhaaS) tool has been spotted targeting Microsoft 365 user accounts of C-level executives…
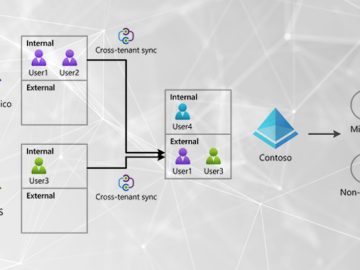
Aug 10, 2023The Hacker NewsThreat Detection / Attack Signal Attackers continue to target Microsoft identities to gain access to connected…
Adaptive Shield announced its Identity Threat Detection and Response (ITDR) capabilities to help organizations mitigate identity-related threats. When paired with…
Aug 10, 2023THNPrivacy / Encryption A widely used Chinese language input app for Windows and Android has been found vulnerable…
Google has moved to speed up the frequency it pushes out security updates and patches for the Chromium open source…
In a recent turn of events concerning the victims of the MOVEit vulnerability, a new threat by the infamous Clop…
Norway-based startup Pistachio on Thursday announced raising €3.25 million (roughly $3.5 million) for its AI-driven cybersecurity training platform. The Pistachio…