Author: Cybernoz
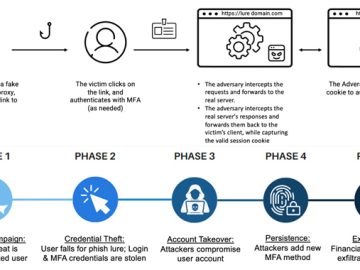
Threat actors are increasingly using a phishing-as-a-service (PhaaS) toolkit dubbed EvilProxy to pull off account takeover attacks aimed at high-ranking…
The Police Service of Northern Ireland (PSNI) is probing a second breach of police officers’ personal data that came to…
Our new IP view offers another point of view on the expanding attack surface Customers often tell us of instances…
The UK Electoral Commission, entrusted with safeguarding voter information, recently faced a complex breach that triggered a vital public notification. …
The code also shows how Yandex can combine data from multiple services. McCrea says in one complex process, an adult’s…
In the last three years, hackers unknowingly seeking data or malware deployment have found a seemingly vulnerable virtual machine that…
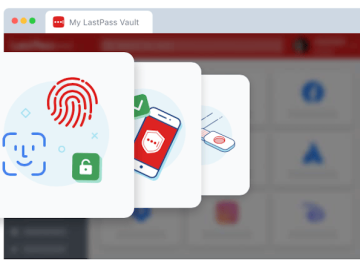
LastPass announced the availability of FIDO2 authenticators, including biometrics, such as finger print or face ID, and hardware keys, for…
Demand for people with technology skills is increasing, but the talent pool is not growing fast enough, according to Harvey…
The US Government House this week launched an Artificial Intelligence Cyber Challenge competition for creating a new generation of AI…
The Biden-Harris Administration has launched a major two-year competition using AI to protect the United States’ most important software, such…
US CISA added zero-day vulnerability CVE-2023-38180 affecting .NET and Visual Studio to its Known Exploited Vulnerabilities catalog. US Cybersecurity and…
The Open Web Application Security Project (OWASP), a non-profit foundation devoted to web application security, recently released the 2023 OWASP…