Author: Cybernoz
Image: Midjourney Google has announced new cellular security features for its upcoming Android 14, expected later this month, that aim…
As 2023’s advancements in technology pose more questions than answers, the industry’s most insightful minds come together at Digital Transformation…
Surge in Kubernetes adoption results in misconfigurations and breaches. Aquasec investigation reveals widespread vulnerability in exposed clusters. Over 350 organizations…
[ This article was originally published here ] The content of this post is solely the responsibility of the author. …
In this podcast, we look at file synchronisation software, with Jimmy Tan, CEO of Peer Software. We talk about how…
Horizon3.ai, a provider of autonomous security testing solutions, announced today that it has raised $40 million through a Series C…
Image: Midjourney Google has announced new cellular security features for its upcoming Android 14, expected later this month, that aim…
Keeper Security released findings from its Privileged Access Management Survey: Deployment Amid Economic Uncertainty. The report explores global insights from IT…
A significant breach has come to light, as cyber threat actors managed to infiltrate a trove of valuable electoral commission…
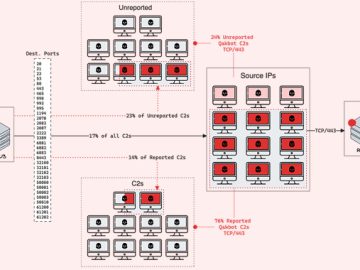
Aug 08, 2023THNMalware / Cyber Threat The operators associated with the QakBot (aka QBot) malware have set up 15 new…
Thank you for joining! Access your Pro+ Content below. August 2023 CW EMEA: Aalto University – where ideas take off…
It is well known that when it comes to cybersecurity, today’s modern network demands solutions that go beyond simple one-size-fits-all…