Author: Cybernoz
Fears around the potential misuse of generative artificial intelligence (AI) tools such as ChatGPT are spreading among IT decision-makers in…
The Royal United Services Institute (RUSI) is an independent UK think tank that has been in existence since 1831. It…
Recent research has shown a remarkable 90% accuracy rate in detecting common online threats and DDoS attacks, which is a…
Agniane stealer, a new information stealer, has emerged on the dark web. This discreet information stealer is being promoted in…
ComplyCube has enhanced its Document Authentication service to counter ‘screen replay attacks’, where scammers attempt to use IDs displayed on…
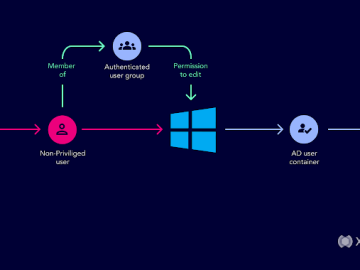
Introduced in 1999, Microsoft Active Directory is the default identity and access management service in Windows networks, responsible for assigning…
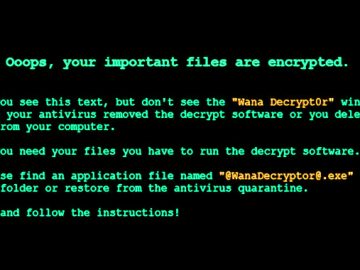
Aug 08, 2023THNEndpoint Security / Malware An unknown threat actor is using a variant of the Yashma ransomware to target…
Let me start with two questions. Do you think ethics is important in the development and application of algorithms or…
The UserSec hacking collective has taken responsibility for orchestrating cyber attacks on two prominent airports in the United Kingdom. The…
Microsoft on Monday published a summary of its artificial intelligence (AI) red teaming efforts, and shared guidance and resources that…
The Tackling the software skills crunch study from Freeform Dynamics recently found that a fifth of organisations consider their development…
The fifth-largest bank in Thailand, the Bank of Ayudhya, also known as Krungsri has come under attack after the K0LzSec…