Author: Cybernoz
IN SUMMARY A basic piece of hardware allows third-party jailbreaking of a Tesla vehicle. The findings came from a security…
04 Aug The World Employs 32,000 CISOs In 2023 Posted at 07:55h in Blogs, Videos by Di Freeze Chief Information…
Aug 04, 2023The Hacker News Privileged Access Management (PAM) solutions are widely acknowledged as the gold standard for securing critical…
Amazon CEO Andy Jassy has credited a shift in its customers’ cloud-spending priorities as playing a pivotal role in helping…
Multiple vulnerabilities in the popular airline and hotel rewards platform points.com could have allowed attackers to access users’ personal information,…
A malicious package that mimics the VMware vSphere connector module ‘vConnector’ was uploaded on the Python Package Index (PyPI) under…
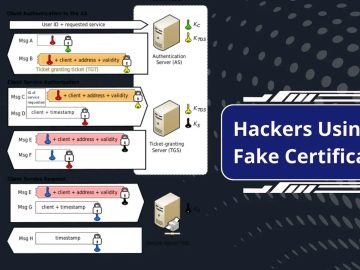
Using fake certificates, attackers gain unauthorized access to corporate network resources. Attackers use such certificates to trick the Key Distribution…
The Cybersecurity and Infrastructure Security Agency (CISA) has published a report which was co-authored by the NSA, FBI, and the…
Cybersecurity researchers have discovered a new bunch of malicious packages on the npm package registry that are designed to exfiltrate…
Google is making it easier for users to remove personal contact information and personal, non-consensual explicit imagery from Google search…
In what appears to be a targeted cyber attack, the NDT SEC hacking group has reportedly aimed at Delta Electronics’…
Threat actors rely on the ‘versioning’ technique to evade malware detections of malicious code uploaded to the Google Play Store….