Author: Cybernoz
New details have emerged about Decoy Dog, a largely undetected sophisticated toolkit likely used for at least a year in…
Apple has issued security patches to address zero-day vulnerabilities that have been exploited in attacks against iPhones, Macs, and iPads…
Stellar Cyber, a cybersecurity company that specializes in providing an Open XDR (Extended Detection and Response) platform, has revealed that…
Google, the technology giant of America has launched a Pilot Program with which it safeguards its employees from state funded…
Jul 25, 2023The Hacker NewsCyber Threat Intelligence How do you overcome today’s talent gap in cybersecurity? This is a crucial…
A hacker forum user was found offering the details of Bank Central Asia account holders. However, a Bank Central Asia…
The notorious hacker group, SiegedSec, has claimed responsibility for a new NATO data breach. NATO is yet to acknowledge or…
Premium Content This content is reserved for premium subscribers of Unsupervised Learning Membership. To Access this and other great posts,…
Five vulnerabilities, two deemed to be critical, have been found in the Terrestrial Trunked Radio (TETRA) standard. TETRA is the…
The CPUs that are based on x86-64 architecture feature XMM registers (128-bit), recently extended to 256-bit (YMM) and 512-bit (ZMM)…
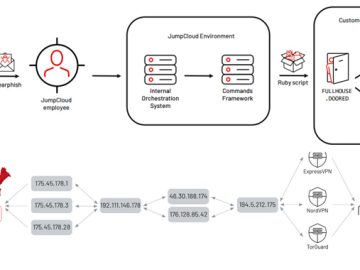
North Korean nation-state actors affiliated with the Reconnaissance General Bureau (RGB) have been attributed to the JumpCloud hack following an…
Two more Post Office Horizon scandal convictions referred for appeal by the Criminal Cases Review Commission (CCRC), which warned against…