Author: Cybernoz
Checkmark researchers have uncovered the first known targeted OSS supply chain attacks against the banking sector. In the first half of…
In a brief email, NCSC spokesperson Miral Scheffer called TETRA “a crucial foundation for mission-critical communication in the Netherlands and…
The chief executives of Commonwealth Bank of Australia and NAB have called out technology giants for anti-competitive behaviour during a…
A China-linked cyberspy group appears to be behind a campaign targeting industrial organizations in Eastern Europe, cybersecurity firm Kaspersky reported…
Generative AI – including services such as ChatGPT and Google Bard – looks like being the next wave of business…
SAP trimmed its full-year outlook for key cloud sales due to lower-than-anticipated transactional revenues in the second quarter. “We’ve seen…
IBM released its annual Cost of a Data Breach Report, showing the global average cost of a data breach reached…
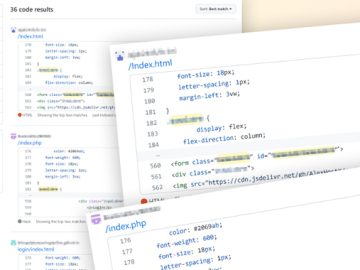
Jul 24, 2023THNSupply Chain / Cyber Attack Cybersecurity researchers said they have discovered what they say is the first open-source…
A North Korean government-backed hacking group penetrated an American IT management company and used it as a springboard to target…
Apple could opt to pull iMessage and FaceTime services in the U.K. in response to the government’s surveillance demands. In…
In a new series of cyber attacks, the infamous NoName hacker group set its sights on Spain, targeting multiple government…
Australia Post is using computer vision technology to detect team members moving into “unsafe zones” at facilities as a site…