Author: Cybernoz
Jul 20, 2023THNMalware / Cyber Threat Cybersecurity researchers have uncovered a new cloud targeting, peer-to-peer (P2P) worm called P2PInfect that…
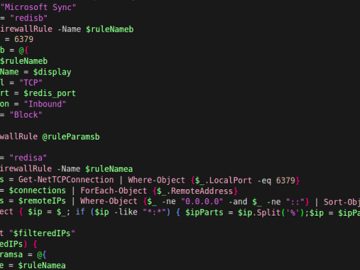
Jul 20, 2023THNCloud Security / Cyber Espionage Microsoft on Wednesday announced that it’s expanding cloud logging capabilities to help organizations…
Russia has issued a ban on the usage of Apple iPhones in government and military sector until further orders. The…
Do you know where your patients’ data lives once it’s in the cloud? Unfortunately, for many healthcare organizations, the answer…
Today’s security operations (SecOps) teams are tasked with protecting progressively sophisticated, fast-paced cyberattacks, according to Vectra AI. Yet, the complexity…
Jul 20, 2023THNSoftware Security / Vulnerability Adobe has released a fresh round of updates to address an incomplete fix for…
On July 11, Adobe coordinated with the vendor to fix several ColdFusion vulnerabilities, including CVE-2023-29298. But it’s been reported that…
The number of successful ransomware attacks and data breach attempts fell by 30% over the last year, the number of…
As the world moves increasingly into a digital realm, the security of data stored in the cloud is an ever-growing…
It has been reported that any individual could potentially deactivate a WhatsApp account by sending an email, and currently, there…
OWASP Foundation has released the 0.9.0 version of Critical Vulnerabilities in LLMs (Large Language Models). A groundbreaking initiative has emerged…
Due to a validation error in Microsoft code, a suspected Chinese attacker was able to access user email from approximately…